tl;dr
We wanted to build a mechanism to capture all the passwords used (successful or not) against RDP to ascertain potential sources of credential theft and if they are organisation specific. This post provides the background on an approach and the steps to build such a system.
Windows Authentication Key Points
We’re not going to cover in detail Microsoft Windows authentication internals, for this post the import headlines are:
- Microsoft introduced Network Level Authentication (NLA) into RDP which adds an initial authentication check to mitigate deeper protocol level vulnerabilities and denial of service attacks.
- NLA use Kerberos or NTLMv2 for this initial step which means by design the password nor the hash are sent to the server in a form which can be quickly recovered. Instead the result of a MD5 HMAC operation is used in a challenge and response protocol with both client and server introduced randomness.
- Mimikatz’s mimilib Security Package callback function SpAcceptCredentials only receives credentials for successful authentications and thus does not receive incorrect passwords.
All of the above were factors which drove the eventual solution design.
Ingredients
Before you start you will need:
- Microsoft Visual Studio
- Windows Server 2012R2 server (tested – but other versions should work)
- a web hook to your favorite communication platform e.g. Microsoft Teams or Slack
- a logo graphic for the organisation you’re collecting intelligence on the behalf of
- .. plus the below code
Note: The resulting system is not intended to be used by real-users but instead deployed as a high signal source of intelligence within the organisation.
Briefly on Microsoft Windows Credential Providers
Windows interactive authentication is extensible via Credential Providers. This is how Microsoft Hello etc. augment traditional username and password authentication to allow you to logon when using the GUI.
By implementing a Credential Provider we can receive the username and importantly the password supplied by the user and flow it through the various authentication mechanisms.
But to be able to leverage Credential Providers in this way we need to disable NLA to receive the clear-text password in the RDP authentication flow.
An Open Source Extensible Credential Provider
There already exists an extensible open source Credential Provider in the guise of pGina (source). As a bonus pGina’s plugin architecture uses C# so is extremely rapid to develop for.
Password Capture Plugin for pGina
A very simple plugin for pGina which does what we want is below. It simply takes the supplied username and password, does a little bit of input sanitization and pumps to a Slack webhook.
Disabling NLA
To disable NLA we:
- Run gpedit.msc
- Navigate to Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Security
- Enable Require use of specific security layer for remote (RDP) connections and select RDP as Security Layer.
- Disable Require user authentication for remote connections by using Network Level Authentication policy.
- Restart the Remote Desktop service.
Installing and Configuring pGina and its Plugin
Initial Steps
- Download and install pGina stable
- Following the pGina plugin developer tutorial replacing HelloPlugin for RDPHoneyPlugin
- Paste in the plugin source code above
- Replace REDACTED with the location of your Slack Webhook
- Compile targeting .NET 4.0
- Place in C:Program FilespGinaPluginsContrib as pGina.Plugin.RDPHoney.dll
pGina configuration
Launch pGina and do the following:
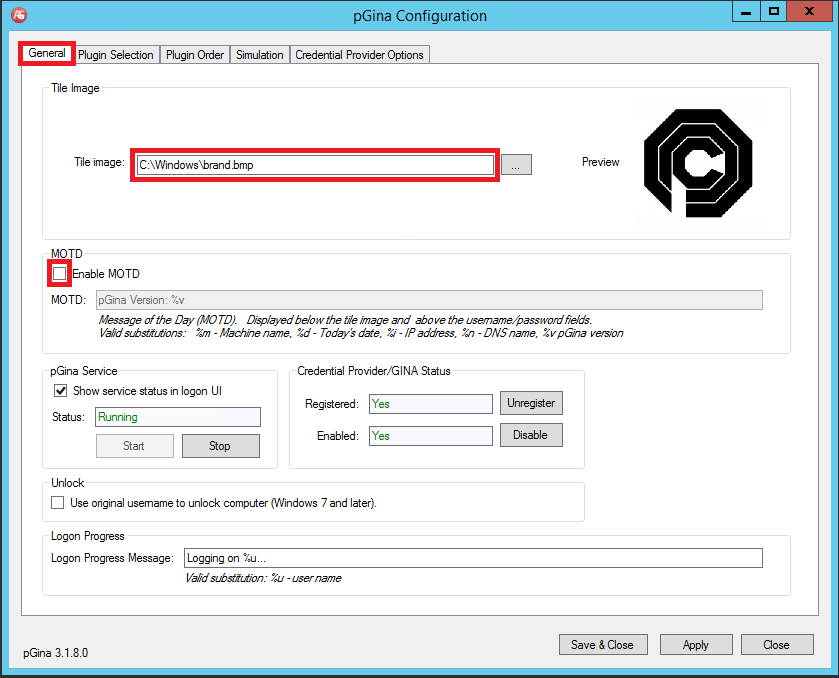
General
- Set the brand image
- Disable the MOTD
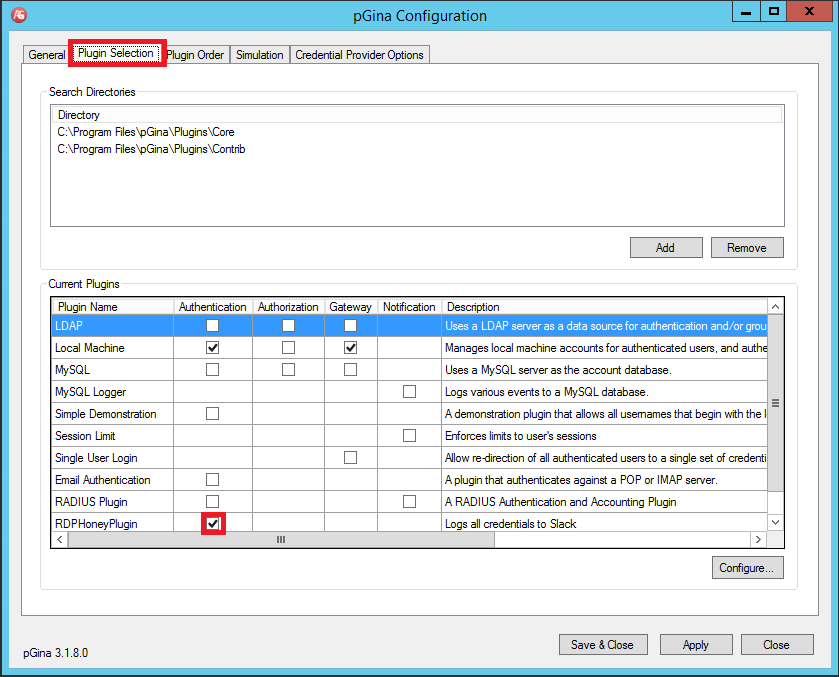
Plugin Selection
- Disable all the other plugins except Local Machine and RDPHoneyPlugin
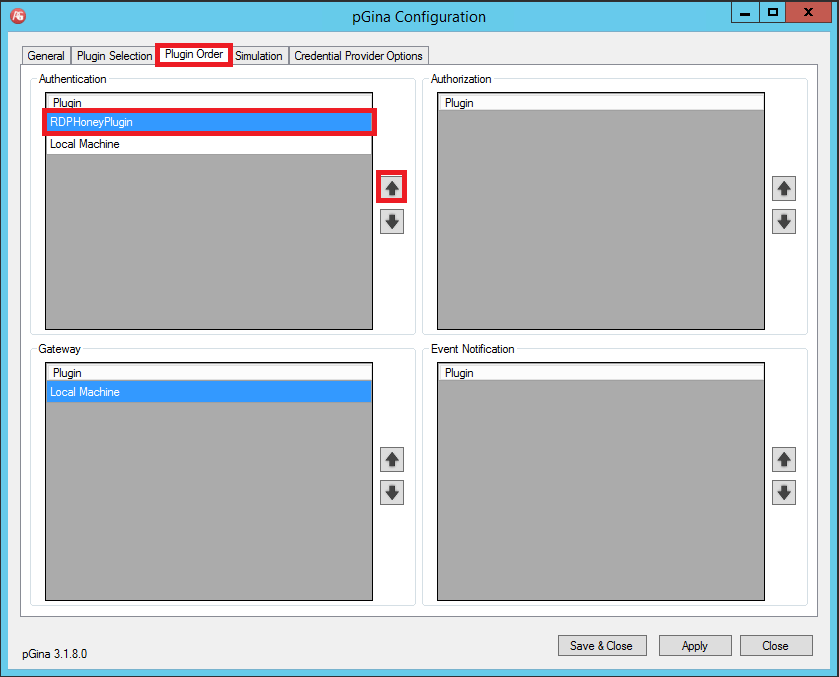
Plugin Order
- Set RDPHoneyPlugin to be the first authentication plugin
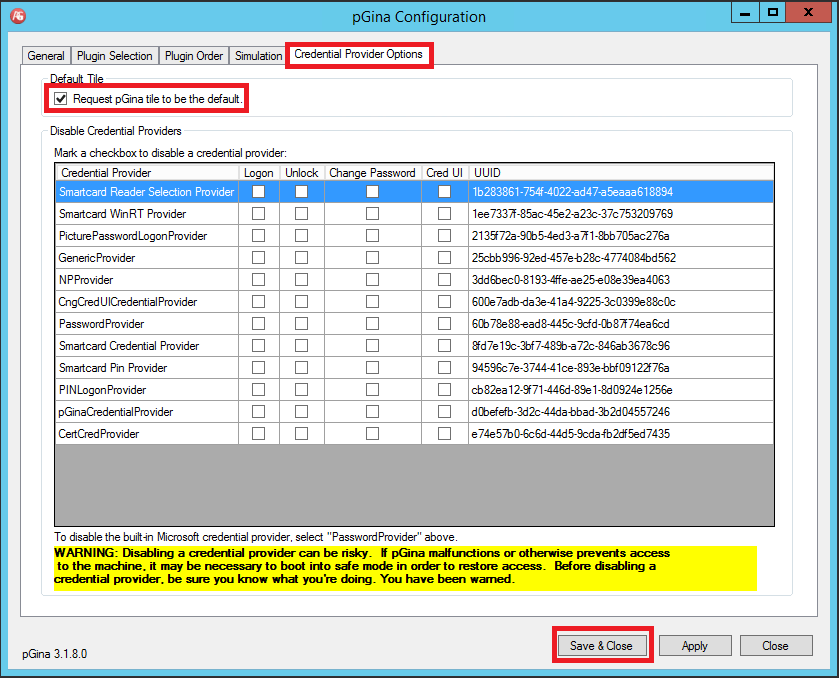
Credential Provider Options
- Make sure that pGina tile is the default
- Hit Save Close
The system is now complete and ready to go.
In Action
What the attacker sees when they connect is:
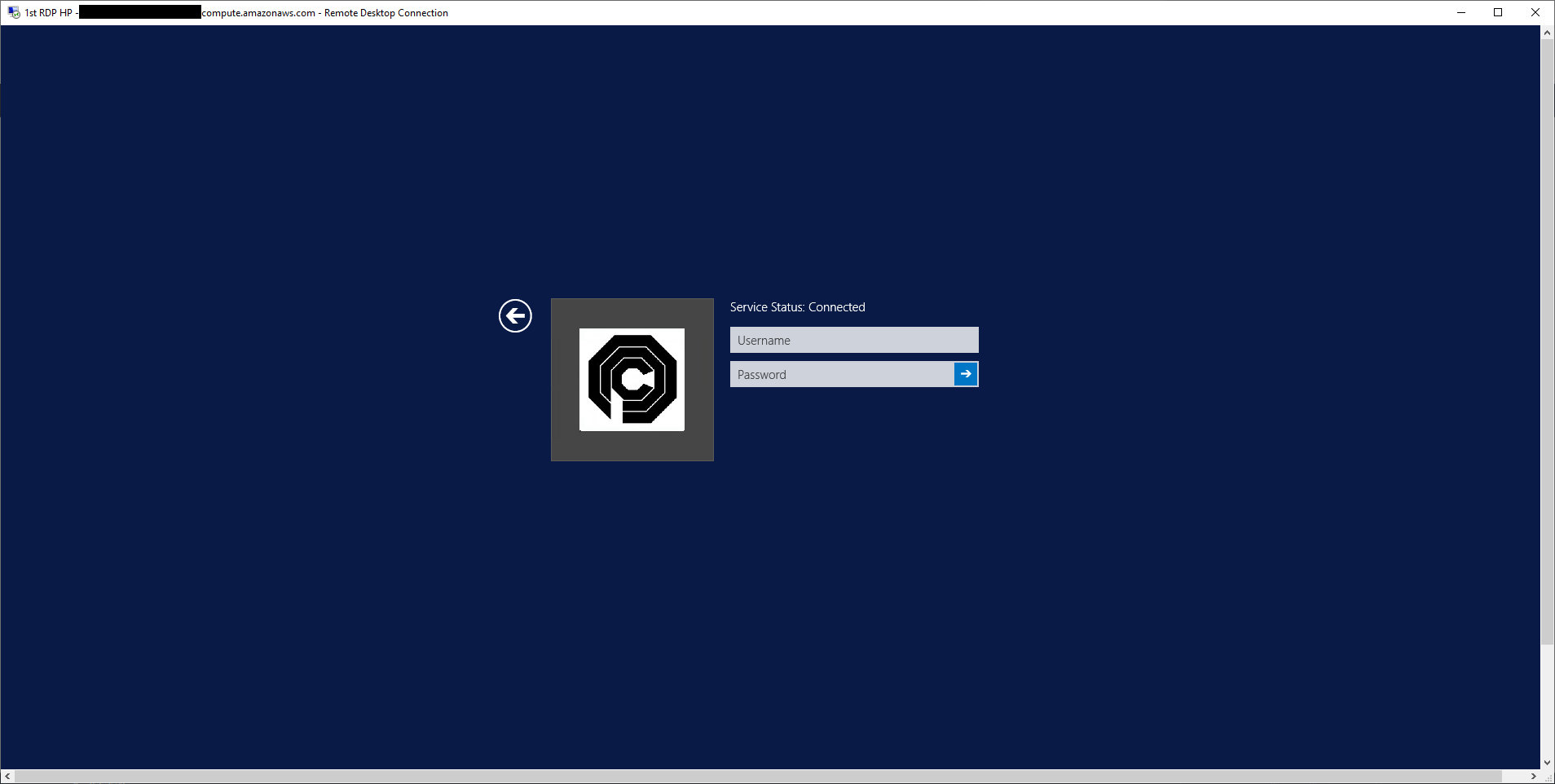
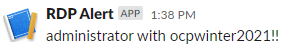
When they provide any credentials the analysts sees in Slack alerts such as:
Summary and Current Research
We’ve shown how to quickly build a functional system capable of collecting all supplied credentials over RDP in order to provide Blueteams with a source of high signal intelligence around potential credential compromises.
The current phase of research is centered around post NLA aspects of Remote Desktop authentication and specifically CredSSP, TSSSP and TSPKG.
Finally a word to the brave. Via pGina you can disable the inbuilt Microsoft password provider to avoid a possible logging bypass i.e. using the inbuilt Credential Provider. We’ve successfully done this without issue. But if you do it comes with all the associated risks.
