tl;dr
- 1,300 phishing campaigns were analysed involving over 360,000 users
- Targets in Charities to be over 3 times more likely to click than the Health Sector
- However once clicked half of all targets were likely to supply credentials regardless
- Best case 1/10 of targets will click a link
- Best case 1/20 of targets will supply credentials
Background
Our hypothesis was that phishing rates would be broadly similar. That is, we expected that there wouldn’t be much variation in phishing success results from organisation to organisation, some users will open the email, click on the link, and enter credentials, others won’t even see read the email. However, analysing the data NCC Group has from its Piranha platform we found a distinct variation on success rates when comparing organisations from different sectors. Targets in Charities were found to be over 3 times more likely to click a link in a Phishing attack than targets in the Health sector, however once a user had been fooled into clicking the link, half were likely to enter credentials regardless of what sector they worked in.
Data Analysed
NCC Group analysed data on over 1,300 simulated phishing campaigns involving more than 360,000 emails, across a wide customer base. This data included a number of tracked events such as clicked link counts, the number of credentials entered, and how long before a campaign target performed one of these events.
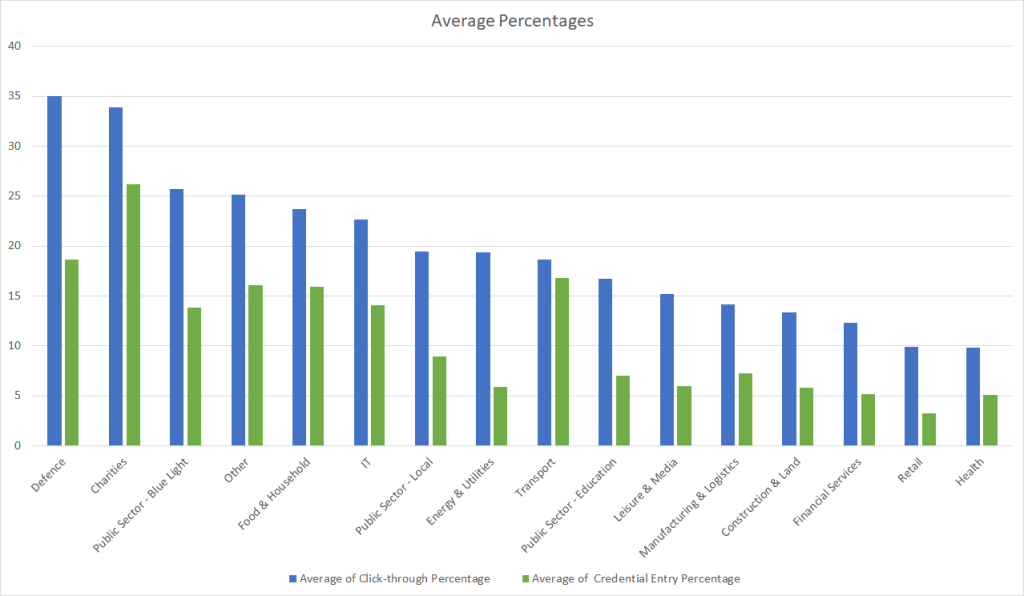
Click Through Rates by Sector
Top Three
The top three sectors by click through rate were Charities, IT Services, and Local Public Sector. Defence, Food Household, and Blue Light also had high click through rates, though the sample size for these sectors were relatively small and may not be representative. Most interestingly, the IT Services sector had a high click through rate, a sector one might expect to be less susceptible to such an attack. Could this be overconfidence that they could handle whatever problem was thrown at them? Perhaps curiosity, and they knowingly clicked through to see how good the phish was that landed in their inbox?
To contrast the three sectors with the lowest click through rates were Retail, Health, and Financial Services with both Health and Retail having less than 10% of targets click through, Retail also had the lowest overall credential capture percentage, averaging just 3.25% of targets.
If a Victim Clicks – No Significant Variance in Credential Entry
There was no marked decrease in the credential entry rate once a user had visited the phishing site though, with targets in IT Services that clicked through then proceeding to enter credentials 62% of the time with the overall rate being 53%.
Financial Services account for the majority of campaigns, likely in part due to the need to remain compliant through regular assessments, these repeat tests and staff training going some way to bring down their click through rate, though as with the other sectors the percentage of credentials captured after a target clicked remained around half of targets, at 42%.
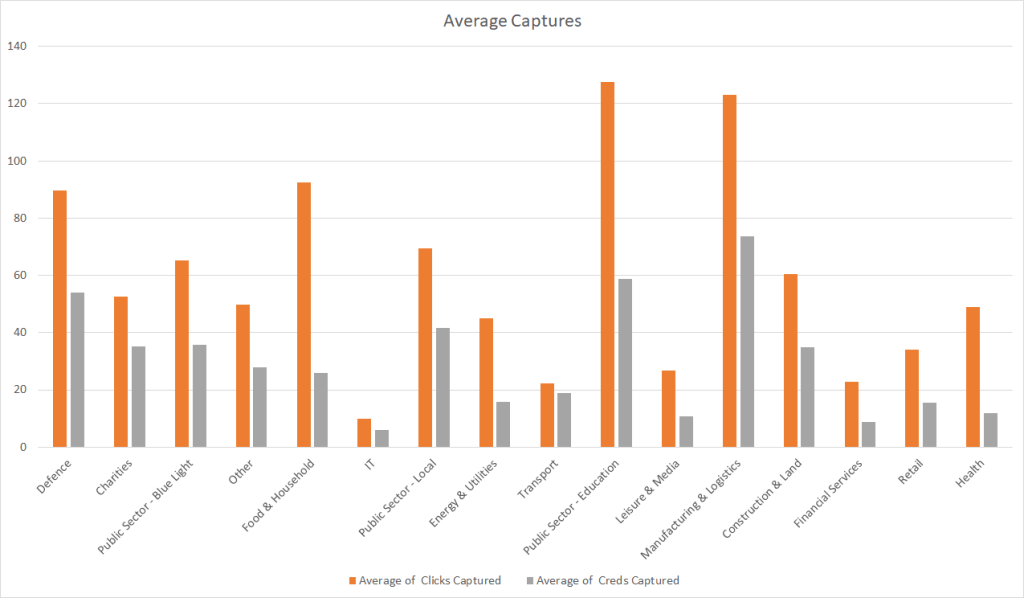
Click to Credential Conversion Ratios
Something else we noticed while analysing the data is the relative consistency when analysing the average number of clicks captured to the number of credentials captured. Overall, we found that the number of credentials captured was around half the number of clicks, this remained true when looking at most sectors, the exceptions being Health and Food Household, where only a third of clicks were followed with credential capture.
Transport had a nearly 1:1 ratio in this analysis, however, the sector represented the smallest sample in the dataset. Given the results from other sectors one would expect that with more data the average ratio to approach 2:1.
Threat Viability and Mitigation Options
Phishing remains a basic, viable and effective threat. The techniques employed by threat actors are a spectrum of sophistication with no sector immune. Once an attacker has valid credentials, the potential attack surface becomes greatly increased within the organisation as actors are able to leverage internal trust relationships to further their access and persistence.
Two-Factor (2FA) or Multi-Factor (MFA) Authentication is the single strongest control when it comes to mitigating the impact of phishing. However, in of itself, it is not a panacea with certain threat actors employing reverse proxies which capture and relay second factors and access to the legitimate site in real-time.
As such cyber resilience should be based upon a combination of:
- Controls such as 2FA/MFA
- Account Misuse Detection through Monitoring and Analytics
- Campaign Detection and Blocking via Controls, Operations and End-User Reporting
- Awareness, Training and Measurement
Want to Run Your Own Phishing Simulations?
NCC Group offers a comprehensive suite of Phishing Simulation solutions from the self-run through to operations run by expert Red Team members. To learn more, visit the NCC Group Cyber Store or speak to your account manager.
