In our latest technical blog series, our DFIR team are highlighting the most prominent Active Directory (AD) threats, describing the tell-tale signs that your AD might be at risk, and give experienced insight into the best prevention and mitigation strategies to shore up your AD security and bolster your digital identity protection.
Last time we took a dive deep into Kerberoasting. Up next, let's unravel the sinister secrets of DCSync attacks - a stealthy technique that can bring your entire Active Directory to its knees.
Definition
Organizations often have multiple Domain Controllers (DCs) for its Active Directory as redundancy. It is also not unknown for DCs to be in place per location to allow authentication and other policies to be made available locally. Where multiple Domain Controllers exist in an organization it is important that every Domain Controller is aware of the changes made in the environment. These changes are typically synced with each Domain Controller using the Microsoft Directory Replication Service Remote Protocol (MS-DRSR).
A DCSync attack is a technique employed by malicious actors to exploit Microsoft’s Active Directory (AD) infrastructure. By mimicking the behaviour of a domain controller (DC), attackers can leverage the (MS-DRSR) protocol using the GetNCChanges function, retrieving credentials from (other) Domain Controllers without accessing the target machine’s memory. In response to the DSReplicaSync request, each DC on the network periodically sends its current objects back to the originating DC. A DCSync attack can be performed from a machine within the domain and the Domain Controller will return the replication data that includes the password hashes. The attack leverages legitimate replication requests, making it difficult to detect without specialized monitoring.
One of the most common tools used for this attack is Mimikatz, locally on a domain joined machine using the lsadump:: /user:<username> command. Remotely it can be done using the Impacket suite with impacket-secretsdump /:@IP, other attack tools can also perform this attack.
How DCSync Works
To perform a DCSync attack, an attacker must have certain rights on Active Directory objects, particularly the ability to replicate directory changes. By default, only Domain Administrators, Enterprise Administrators, Administrators, and Domain Controllers groups have the required privileges.
Here’s a high-level step-by-step breakdown of a DCSync attack:
- Compromise a High-Privileged Account: The attacker first gains access to an account with elevated privileges, such as a member of the Domain Admins, Enterprise Admins, or Administrators groups.
- Request AD Replication: Once the attacker controls an account with replication rights, they use Mimikatz or a similar tool to request Active Directory replication. The tool sends a request to the domain controller, asking it to sync specific directory objects such as user account information and password hashes.
- Receive and Use Credentials: The domain controller, believing it is communicating with another authorized domain controller, responds with the requested data. This data includes password hashes for specific users, which the attacker can then crack or use directly in attacks like pass-the-hash or pass-the-ticket.
This attack is mapped as T1003.006 on Mitre ATT&CK. OS Credential Dumping (T1003) DCSync (006) https://attack.mitre.org/techniques/T1003/006/
Detection & Hunting
Detecting DCSync attacks is challenging because they leverage legitimate AD replication functionality. However, there are some key indicators that can help in identifying suspicious activity:
Windows Security Log Event ID 4662: An operation was performed on an object.
In the Windows Security logs (C:\Windows\System32\winevt\Logs\ Security.evtx), this event indicates a request for directory replication. Specifically, watch for access rights to the following GUIDs:
- {1131f6aa-9c07–11d1-f79f-00c04fc2dcd2} — DS-Replication-Get-Changes
- {1131f6ad-9c07–11d1-f79f-00c04fc2dcd2} — DS-Replication-Get-Changes-All
- {89e95b76–444d-4c62–991a-0facbeda640c} — DS-Replication-Get-Changes-In-Filtered-Set extended right
The before mentioned strings can be found on the properties of the event 4662.
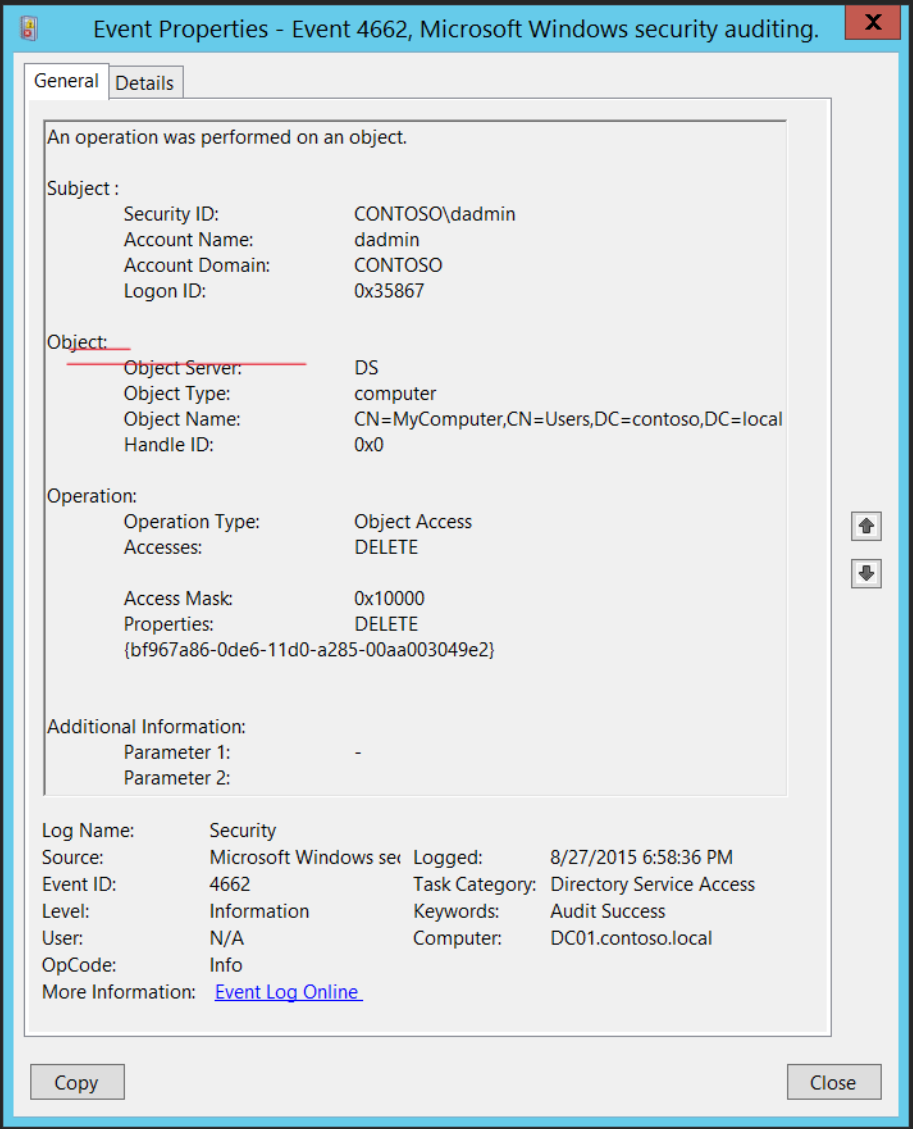
Event 4662 illustration
There are also Sigma rules created to detect this activity: https://github.com/mdecrevoisier/SIGMA-detection-rules/blob/main/windows-active_directory/win-ad-replication%20privilege%20accessed%20(SecretDump%2C%20DCsync).yaml
Preventing DCSync attacks
These attacks are complex to detect both whilst they are happening or after they have occurred, so it is important to focus on preventing them or at least making them more difficult to carry out. Unfortunately, there is no easy way to do this, instead a series of actions that will harden the AD environment are recommended.
DCSync requires that the attacker have Replicating Directory Changes and Replicating Directory Changes All permissions in AD. These permissions should be restricted to only domain controllers and trusted administrative accounts. Review and limit accounts with high privileges like Domain Admins, Enterprise Admins, and groups that have replication permissions.
Implement the Principle of Least Privilege, ensuring that only necessary accounts have Domain Admin and Enterprise Admin privileges, remove users or service accounts from these groups that do not need this level of access.
Monitor and Audit for Unusual Replication Requests
Monitor for unusual requests for directory replication or unusual use of replication permissions. The easier way to have visibility over these events is using Sysmon. Log and track any use of the DRSUAPI (DsGetNCChanges) function, which is used in DCSync attacks.
Enable Advanced Auditing for "Directory Services Replication" and "Logon/Logoff" events.
Lastly audit high-privileged AD groups for user accounts that should not be included. The following groups are considered highly privileged and at high risk of abuse.
- Domain Admins
- Enterprise Admins
- Administrators
- Schema Admins
- Backup Operators
- Account Operators
- Server Operators
- Domain Controllers
- Print Operators
- Replicator
- Enterprise Key Admins
- Key Admins
Conclusion
These kinds of attacks are performed when the attackers already have a good foothold on the network and accounts with an important level of access. Sometimes the attacker already has Domain Admin credentials and performs this attack to harvest more passwords or target a specific account, in any case, upon detection is important to act swiftly to prevent further escalation of the compromise.
These attacks are very hard to detect and even with detection rules in place the results must be further investigated to discard false positives.
Learn more about the following services to help you proactively prepare against Active Directory attacks:
Signup to our free Threat Intelligence for regular updates on the latest threat actors or contact NCC Group if you have any further queries.