tl;dr
In this post we show how to import WStalker output into Burp Suite and the Logger++ extension to build a sitemap from a recorded session for use in Intruder and Repeater.
Importing into Burp Suite via Import To Sitemap
In our previous blog post we used WStalker to create the file wstalker.csv, containing information about each request:
[REQUEST_IN_BASE64],[RESPONSE_IN_BASE64],METHOD,URL.
Now, we need to import this information into our favourite testing tool so we can manipulate each request, iterate parameters, etc. For this reason, we created a Burp Suite extension called “Import To Sitemap“, which is now available in the official BApp Store.
Once the extension has been installed and loaded into Burp, an additional tab called “Import Sitemap” is added. This new tab has a number of buttons to select and load the CSV file.
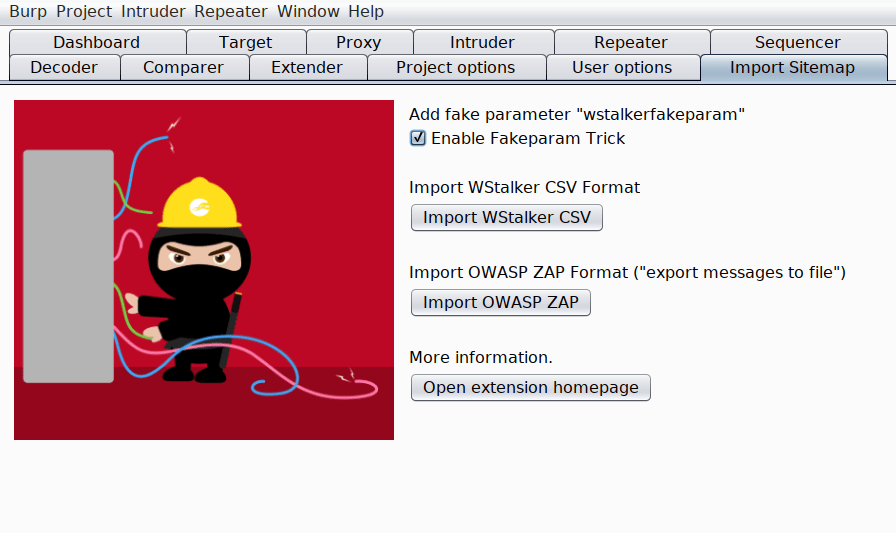
To import the content of the WStalker CSV file into Burp’s Sitemap, we just need to click on “Import WStalker CSV” and choose the file. It can take some seconds to load all the information depending on the number of requests to be imported. After that, requests and responses will appear in the Sitemap. Once imported to Sitemap, you can send the request to repeater or intruder to use the well-known Burp Suite capabilities.
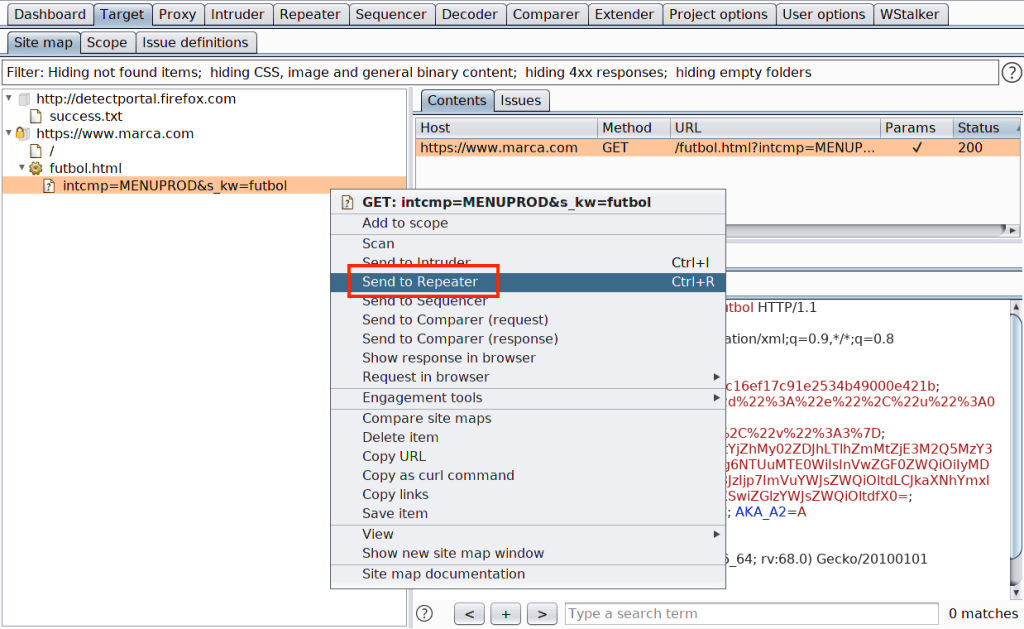
Importing from OWASP ZAP to Burp
As you may have noticed, there is another button “Import OWASP ZAP”. This feature was added to the extension since we found that some clients preferred to use the open source proxy OWASP ZAP and share its files.
Since the standard session files used by ZAP are binary and parsing them would require a reverse engineering process, we need to export the content in a different format.
The following steps are needed:
- Open OWASP Zap with the HTTP requests you want to export.
- Go to the “History” tab and select all the desired requests (usually all of them).
- Go to menu “Report” and then “Export Messages to File…”
- Choose folder and file name.
The resulting file should have the following format:
==== 1 ==========
GET https://whatever.com/foo/ HTTP/1.1
[REQUEST]
[RESPONSE]
==== 2 ==========
[...]This file can now be imported into the Sitemap through the “Import OWASP ZAP” button.
Hacking Around Same URL Limitations in Burp
There is also a checkbox “Enable Fakeparam Trick” which is enabled by default. This option exists because the Burp Suite API used to import requests into Sitemap does not allow adding two different requests with the same URL, even when they have differences in the body. The best way we found to work (hack) around this limitation was to add a fake parameter “wstalkerfakeparam” in the URL with a unique UUID per request. With this workaround, every request will have a different URL, so none of them will be lost in the process of importing.
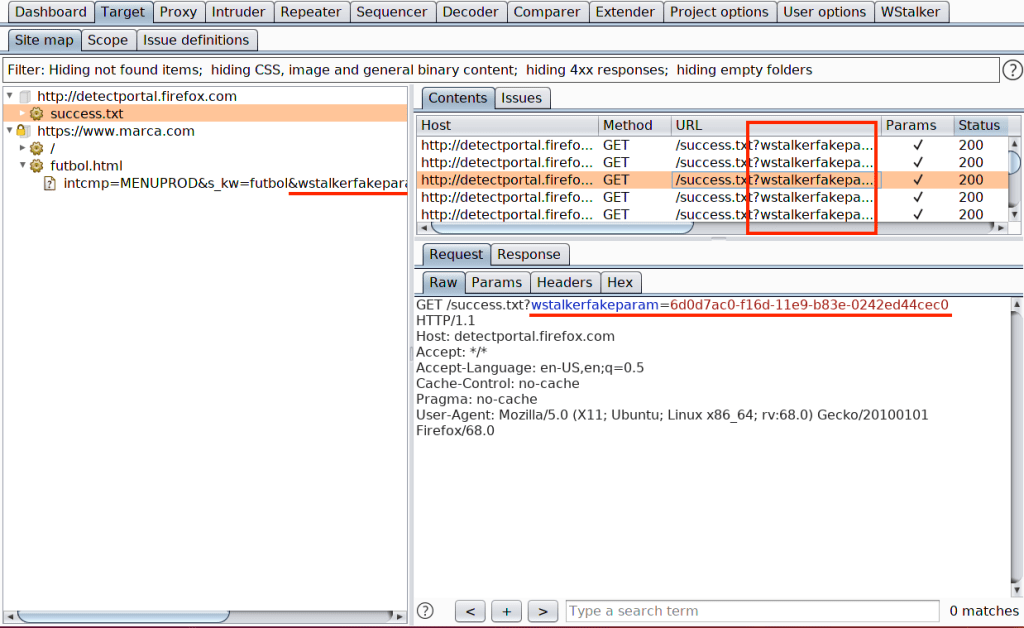
This fake parameter can be removed later on in Repeater or Intruder if necessary. This can also be disabled by unticking the checkbox, but keep in mind that you should verify that every request was imported.
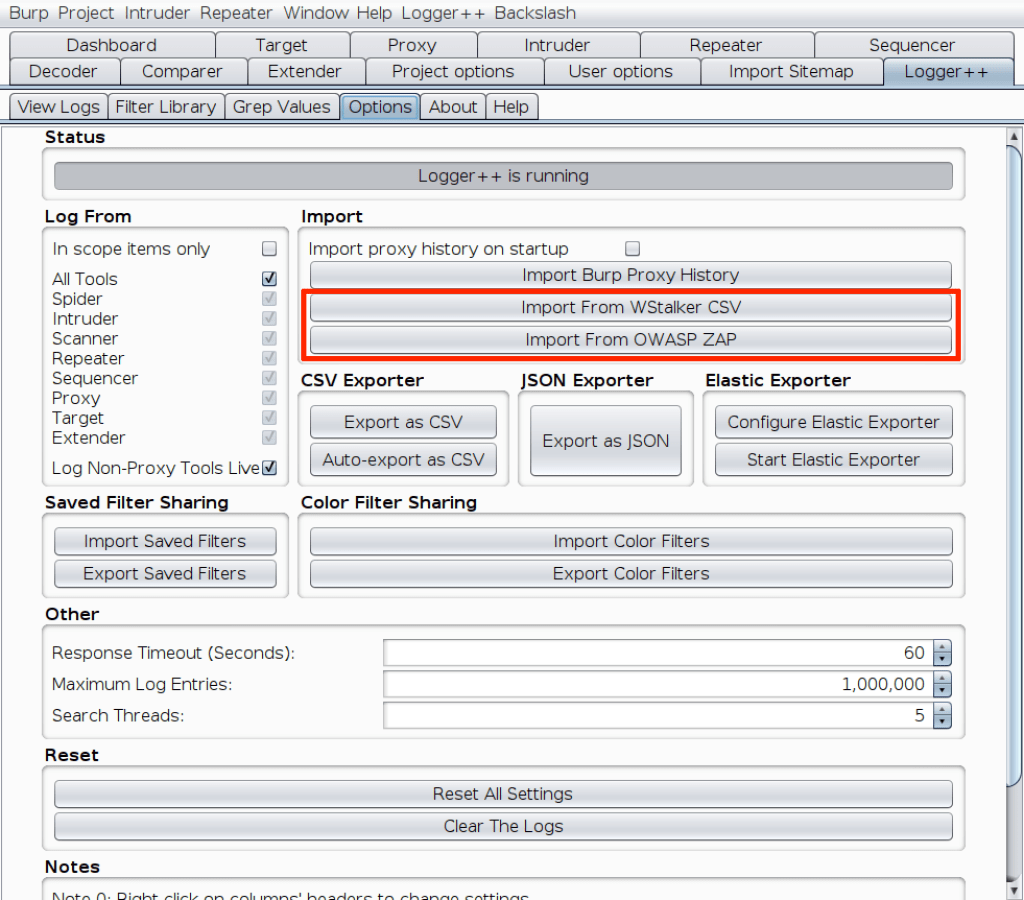
Importing WStalker and OWASP ZAP into Logger++
Finally, we added the same importing features to the well-known Logger++ Extension (also available in the BApps Store), so we can also use its amazing filtering capabilities.
Winning..
Using WStalker, Import To Sitemap and Logger++ is a winning combination.. go forth and conquer those Web APIs!
