In this blog post, we introduce LTair, a tool that allows NCC Group to perform different attacks on the LTE Control Plane via the air interface. It gives NCC the capability to assess the correct implementation of the LTE standard in operators’ systems and user equipment.
LTair
The LTair tool is the main outcome of an internal research whose main objective was to develop a tool and a methodology to assess the security posture of different elements of an LTE network, including the user equipment, via the most exposed interface: the air.
The attacks or vulnerabilities described in this post are known vulnerabilities extracted from several public papers (see “Public Papers” section).
LTair is based in the open source framework SRSran. This framework is able to emulate a complete LTE network: a rogue LTE base station (eNodeB), a full core network and a User Equipment (for example, a mobile phone). LTair can act as a User Equipment when the target is an operator, or as an operator when the victim is a User Equipment.
These attacks are performed over the air, this means that a transceiver compatible with SRSran framework should be used, a list of compatible devices and hardware options can be found in the SRSran documentation page.
For a better understanding, the identifiers from the attack included in this post have been simplified. More complex identifiers are used in real scenarios.
LTair can act as a User Equipment when the target is an operator, or as an operator when the victim is a User Equipment. The following icons will be used in each case:
Some of the most known attacks implemented include:
Capture sensitive information in eNodeB paging broadcast
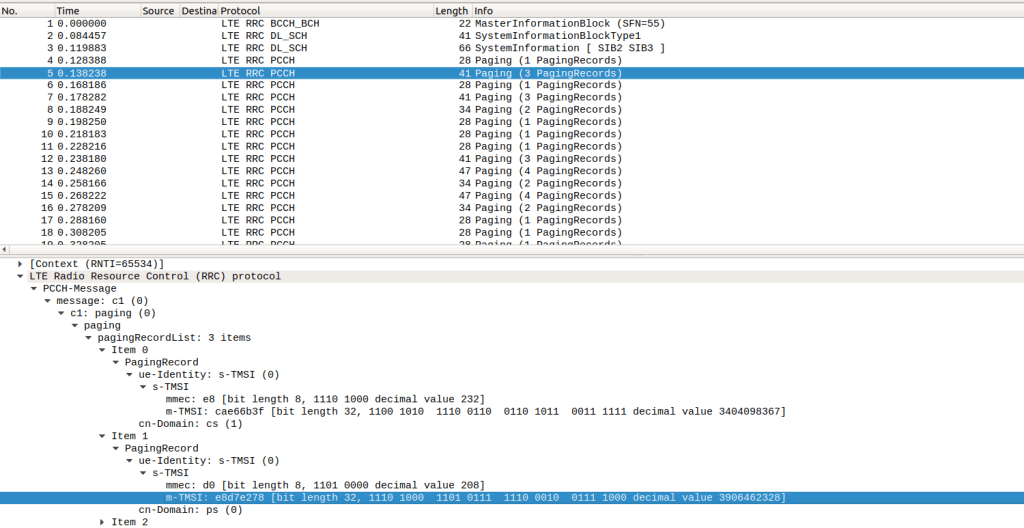
LTE base stations (eNodeBs) transmit broadcast paging messages that can be captured by anyone listening in its frequency. These paging messages contain subscriber’s temporary identifiers (S-TMSIs), but they could also contain permanent identifiers (IMSIs). Permanent identifiers should never be transmitted in broadcast messages, since they uniquely identify a subscriber. If an attacker knows a subscriber’s permanent identifier and captures a paging message with the same IMSI on it, the subscriber’s location could be compromised.
Given a frequency, LTair is able to capture and monitor paging messages looking for subscriber’s permanent identifiers, detecting vulnerable operators.

The following screenshot shows paging requests captured and inspected with Wireshark:
Persistence of temporary identifiers after attachment procedure
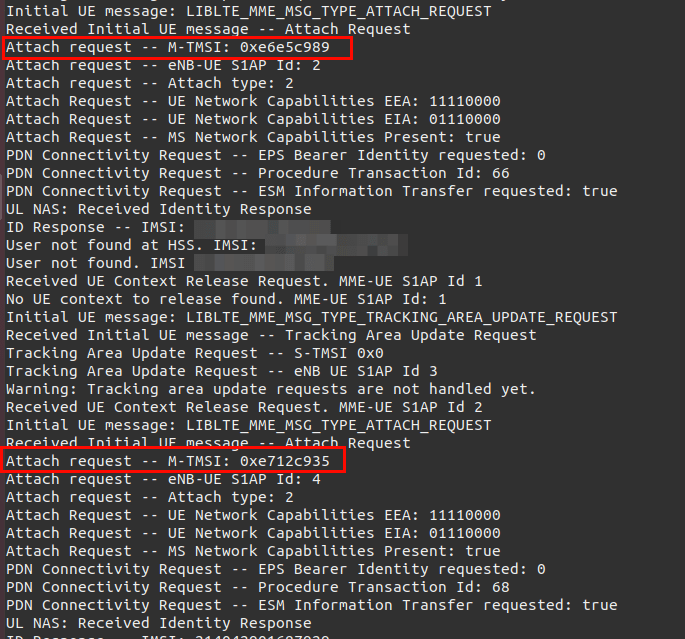
Since subscriber’s temporary identifiers are included in broadcast paging messages, they need to be changed regularly to protect the privacy of the subscriber. If this identifier is kept unchanged for a long period of time, an attacker could capture paging messages, extract their temporary identifier and locate a subscriber.
With LTair, it is possible to verify if temporary identifiers change after a new attachment procedure.
The following example shows how the value of M-TMSI changed from the first attachment to the second:
Blind Denial of Service
There are two variants of this attack: in the first one, the victim is in “RRC Connected” state. This means that the user is “active”, using their phone. In the second variant, the victim is in “RRC Idle” state, meaning that the user is not transmitting or receiving data from/to the operator’s network, and it is waiting to receive new data from the network. A user “wakes up” and moves from “RRC Idle” to “RRC connected” when a paging message with his/her temporary identifier is received.
In both scenarios, this attack denies a targeted subscriber by establishing RRC connections spoofed as the victim UE, using his/her temporary identifier (in the diagram below, the victim temporary identifier would be “123”). When the operator receives a new radio request with the same temporary identifier, the previous radio connection is released and the victim is blindly disconnected from the network. Since the complete attachment is not performed, an attacker does not need keys to attach to the network (a valid SIM card), just the RRC channel needs to be established.
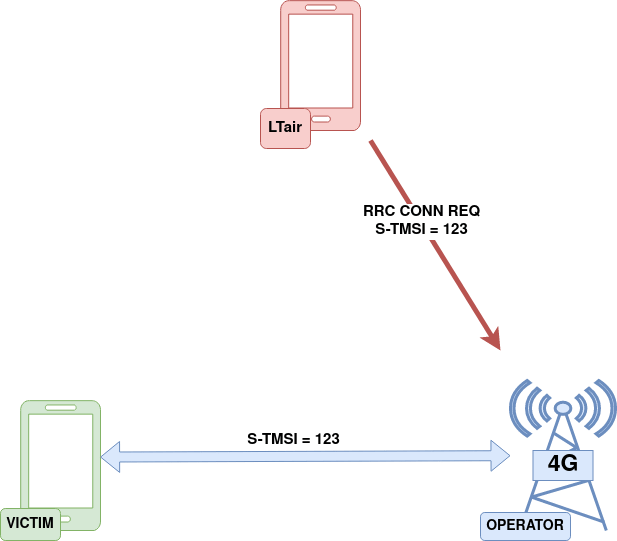
It must be noted that this attack is performed against the operator’s core network and denies service to a subscriber, so the victim and the attacker can be several kilometers apart.
Downgrade from 4G to 3G
The objective of this attack is to force a target user to downgrade its connection from LTE to 3G or, if 3G is not available, to 2G.
The attacker places a rogue 4G base station (eNodeB) close to the victim. When the target User Equipment (UE) detects a closer eNodeB, it initiates a TAU (Tracking Area Update) procedure. However, the rogue eNodeB responds with a TAU reject message, with cause number 7 which corresponds to “LTE services not allowed”. Since TAU reject messages are not protected and there is no need of mutual authentication, the UE accepts and sets the status to “EU3 ROAMING NOT ALLOWED”, considering the USIM UE invalid for LTE services until it is rebooted, the USIM is re-inserted or the airplane mode is turned on and off.
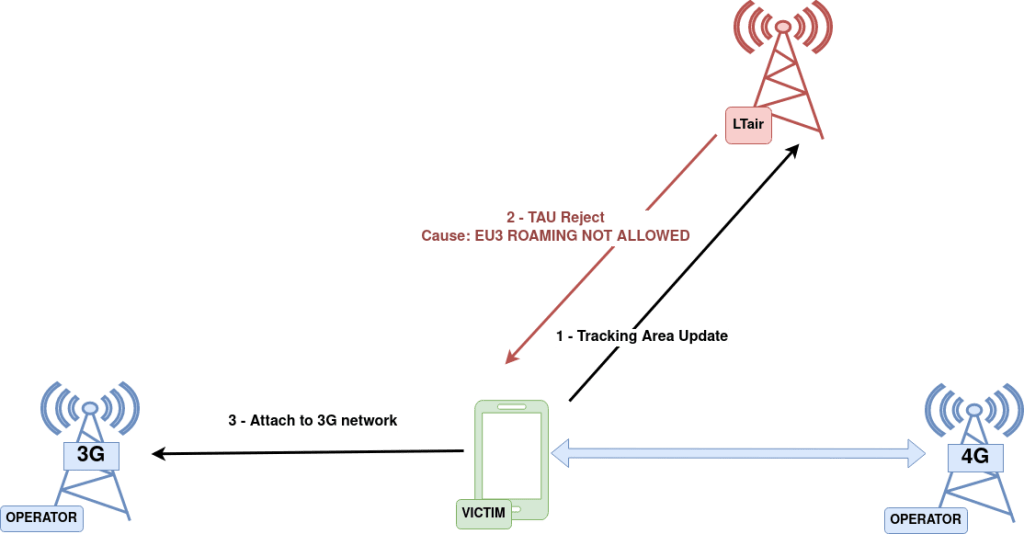
A successful downgrade attack can be seen in the following video. On the left, a mobile phone is plugged to the laptop where LTair was executed. It is connected to a 4G network, as indicated by the network icon on the top right. Then, LTair is executed and, when a TAU request is received, LTair replied with with a TAU reject cause number 7. Suddenly, the phone looses 4G connection, downgrading to 3G.
Denying all network services
The objective of this attack is to deny all network services to a target UE, including voice calls and SMS.
The same procedure from the “Downgrade from 4G to 3G” attack is followed. However, in this case, the rogue eNodeB responds with a TAU reject message with cause number 8, which is “LTE and non-LTE services not allowed”.
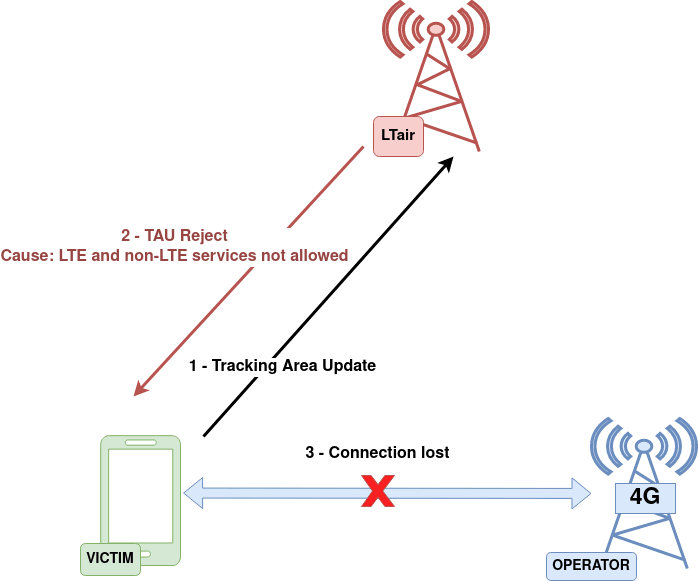
The same setup as the previous attack was employed. The phone, on the left side of the screen, was connected to a 4G network. Upon executing LTair, a TAU request was received, and LTair responded with a TAU reject cause number 8. This time, as indicated by the top-right icon on the phone, the connection to any network was lost.
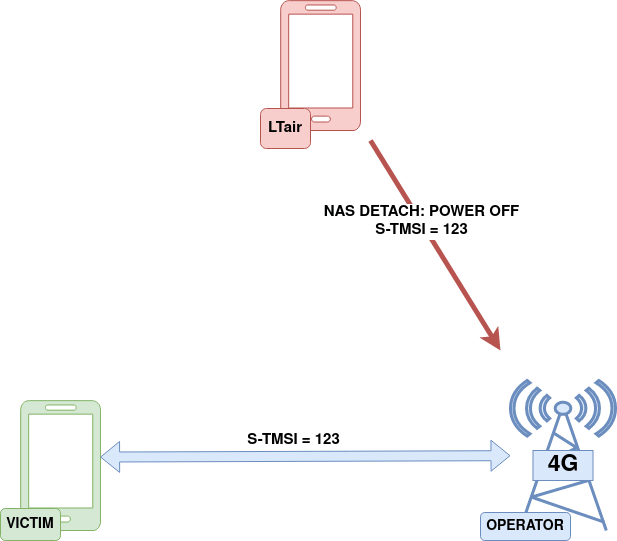
Detach a victim from the network through spoofed UE-initiated Detach message
The attacker sends UE Detach Request message with an action of power-off to MME by putting victim’s S-TMSI in the message. The MME verifies the integrity of the messages, however, detach messages with power-off type are processed even if their integrity check fails. Once the MME receives this message, it releases victim’s network resources.
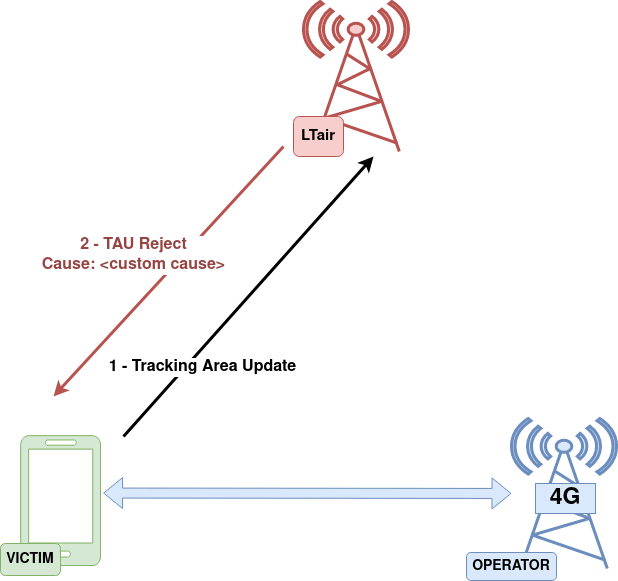
TAU Reject – custom cause
“Denying all network services” and “Downgrade from 4G to 3G” attacks are based on responding TAU reject with different causes when a TAU request is received. In this case, a custom cause can be established. The behaviour of the network varies depending on the cause. This attack could be used to verify the correct implementation of the Tracking Update Procedure on User Equipments.
Glossary
- UE: User Equipment.
- MME: Mobility Management Mobility.
- IMSI: Mobile Subscriber Identity.
- S-TMS: Serving Temporary Mobile Subscriber Identity.
- eNodeB: 3GPP-compliant implementation of 4G LTE base station.
- TAU: Tracking Area Update.
- DoS: Denial of Service.
- 3G: third-generation.
- 4G: forth-generation.
- LTE: Long Term Evolution, sometimes referred to as 4G LTE.
- RRC: Radio Resource Control.
Public Papers
- Sørseth, Christian et al. “Experimental Analysis of Subscribers’ Privacy Exposure by LTE Paging.” Wireless Personal Communications 109 (2018): 675 – 693.
- Rupprecht, D., Kohls, K.S., Holz, T., Pöpper, C. (2020). Call Me Maybe: Eavesdropping Encrypted LTE Calls With ReVoLTE. USENIX Security Symposium.
- Kim, H., Lee, J., Lee, E., Kim, Y. (2019). Touching the Untouchables: Dynamic Security Analysis of the LTE Control Plane. 2019 IEEE Symposium on Security and Privacy (SP), 1153-1168.
- Shaik, A., Borgaonkar, R., Asokan, N., Niemi, V., Seifert, J. (2015). Practical Attacks Against Privacy and Availability in 4G/LTE Mobile Communication Systems. ArXiv, abs/1510.07563.
- Raza, M.T., Anwar, F.M., Lu, S. (2017). Exposing LTE Security Weaknesses at Protocol Inter-layer, and Inter-radio Interactions. Security and Privacy in Communication Networks.
