Here at NCC Group we work with raw bytes a lot! As I couldn’t find a good tool to manipulate, encode and decode easily I set about writing Pip3line a while back. While it has been available for a while as open source I’ve not really discussed it outside of NCC hence this post.
What is pipeline?
What is Pip3line? It’s a raw bytes manipulation utility, able to apply well known and less well known transformations from anywhere to anywhere (almost). Or put another way it is a tool for manipulating raw bytes blocks, and is able to apply diverse transformations to them.
Its main usefulness is for security research, penetration testing, reverse-engineering and binary analysis purposes.
What does it looks like? What can it do?
On a Linux system the main window would look like this:
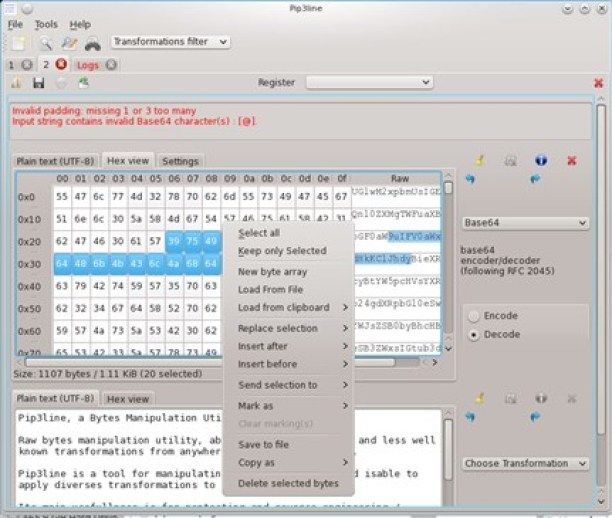
Current transformations list include classic decoders such as Base64/32/hex to simple cryptographic ciphers, and includes common hashes algorithms as well as obfuscation techniques.
Easy to use, but still offering some tweaking for most transformations, it also has the ability to save/restore a configured transformation chain for future used.
The tool is also able to apply a transformation chain `en masse` to either a file, or data blocks received from a TCP socket, a Named Pipe (Windows) or a UNIX Socket (UNIX/Linux) via the mass processing utility
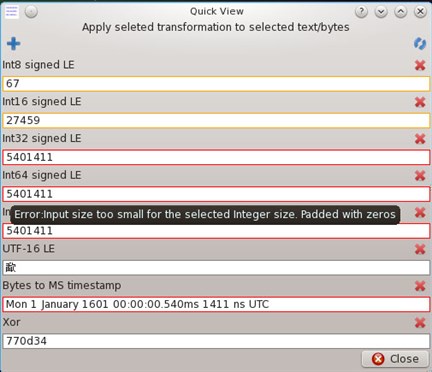
To help reverse engineering, it has a powerful quick view functionality is present, which will automatically apply a transformation to the current selection.
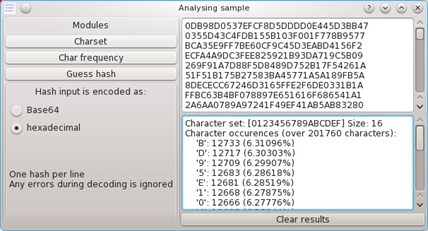
The text analysis functionality gives you some basic information from your input.
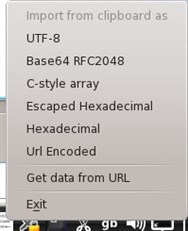
Finally the tool allows you to import/export bytes data easily, either via the Tray Icon, the context menu, or the pre-configured shortcuts.
It’s extensible too!
Pip3line was designed to be extensible from the output, it allows you to create your own transformations by using the C++/QT plugin API.
Alternatively you can just use the powerful Python 2.7 3 plugins to load your own Python scripts.
Where to get it from?
You can get the source code from the NCC Group git hub repository here:
If you’re after pre-built binaries for Linux or Windows it can be found here:
Note:Read the download instructions carefully
Wants to know more?
- Native plugin API – https://github.com/nccgroup/pip3line/wiki/Native-plugin-API
- Python plugins – https://github.com/nccgroup/pip3line/wiki/Python-plugins
- Shortcuts list – https://github.com/nccgroup/pip3line/wiki/Shortcuts-list
As always we’d love to hear your feedback and any ideas you have for features via the comments.
Published date: 22 April 2013
Written by: Gabriel Caudrelier
