Summary
Tl;dr
This post will delve into a recent business email compromise engagement handled by NCC Group’s Digital Forensics and Incident Response (DFIR) team, which saw the compromise of 12 users’ Microsoft 365 accounts.
Below provides a summary of findings which are presented in this blog post:
- Initial access via phishing email
- Maintain persistence on a Microsoft 365 account
- Inbox rule creation
- Email deletion
- Harvesting Microsoft 365 credentials
Incident Overview
Initial access was gained via a successful phishing email sent from a user from a supplier. The user’s email had been compromised resulting in phishing emails being sent to external recipients. One of the external recipients was patient zero in the engagement NCC Group responded to.
Patient zero clicked the link in the spearphishing email, provided their credentials giving the threat actor access.
The threat actor was observed using the axios/1.7.2 user agent.

This same user agent was observed in the interactive sign-in logs for the total 12 compromised users in this engagement.
The Axios website outlines that Axios is a promise-based HTTP client for node.js and the browser. The client supports the ability to intercept, transform and cancel request and response data. As outlined in this article, the Axios infrastructure can be used to capture credentials and possibly session tokens, thus allowing the threat actor to satisfy the MFA requirement in this attack. Various IOCs observed in this attack were listed in the Field Effect article above.
Once the threat actor had access to patient zero’s account, they registered a new authenticator app with notification and code, created new inbox rules to move emails that would have potentially raised the user’s suspicions and uploaded documents to the user’s personal SharePoint site. One of the documents uploaded was used as an attachment in a phishing email which the threat actor sent to hundreds of recipients.
Timeline
T + 0 - Initial Access gained
T + 3 days - Persistence via Registration of Authenticator App
T + 6 days - First lateral movement attempt
T + 25 days – Successful second lateral movement attempt
Mitre TTPs
Resource Development
T1586.002 - Compromise Accounts: Email Accounts
The account belonging to a user who worked for a supplier was compromised and used to send phishing emails.
Initial Access
T1566.001 - Phishing: Spearphishing Attachment
Patient zero received a phishing email from a user who worked for a supplier. The email subject was <NAME> shared <FILE NAME> with you and contained a link to a document hosted on the external user’s personal SharePoint site.
T1078.004 - Valid Accounts: Cloud Accounts
Patient zero clicked the link in the phishing email and subsequently the threat actor successfully logged into their account.
T1204.002 - User Execution: Malicious File
The malicious PDF attached in the initial phishing email was clicked on by patient zero. This user received an email titled 20289990 is your Microsoft OneDrive verification code to access the malicious PDF.
Persistence
It is possible the threat actor was able to maintain access to the compromised users accounts by clicking Yes when presented with the Stay signed in option after completing MFA. The Keep user signed in feature was enabled in the victim’s environment.
T1078.004 - Valid Accounts: Cloud Accounts
12 users’ Microsoft 365 accounts were accessed by the threat actor.
T1098 - Account Manipulation
The threat actor, using the 156.96.154[.]190 IP address, registered new security information on patient zero’s account. This activity was represented in the logs as SoftwareTokenActivated and Authenticator App with Notification and Code.
Prior to this activity, the threat actor accessed the My Signins application which is the location where new MFA authentication methods can be added.
Defence Evasion
T1564.008 – Hide Artifacts: Email Hiding Rules
Inbox rules were created by the threat actor to move emails containing certain keywords and from specific senders to different locations.
The below mailbox rule was created across all compromised accounts and specified that emails containing any of the below keywords were moved to the Rss Feeds folder and marked as read.
"Parameters":[{"Name":"AlwaysDeleteOutlookRulesBlob","Value":"False"},
{"Name":"Force","Value":"False"},{"Name":"MoveToFolder","Value":"Rss Feeds"},
{"Name":"Name","Value":"..."},
{"Name":"SubjectOrBodyContainsWords","Value":"hack;hacker;hacked;password;compromised;compromise;phishing;reset;spam;scam"},{"Name":"MarkAsRead","Value":"True"},
{"Name":"StopProcessingRules","Value":"True”}]
On a couple user’s accounts, the threat actor created inbox rules to move emails from specific users to the RSS Subscriptions or Rss Feeds folders.
T1070.008 – Indicator Removal: Clear Mailbox Data
The threat actor was observed deleting emails especially those warning the affected users about the phishing email (see Lateral Movement).
Credential Access
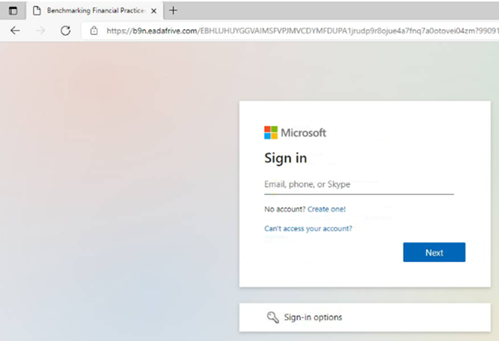
T1056.002 – Input Capture: GUI Input Capture
If users clicked on the link in the phishing email sent out by the threat actor, they were taken to surl[.]li and then redirected to a fake Microsoft login page (see below) where they were prompted to enter their Microsoft 365 credentials.
Figure 2 - Fake Microsoft login page
Based on the screenshot and the evidence observed during the investigation, it is highly likely the threat actor’s motivation of this campaign was to harvest credentials specifically Microsoft 365 credentials.
Lateral Movement
T1534 – Internal Spearphishing
25 days after initial access, the threat actor sent a phishing email from patient zero’s account to both internal and external recipients, as seen below.
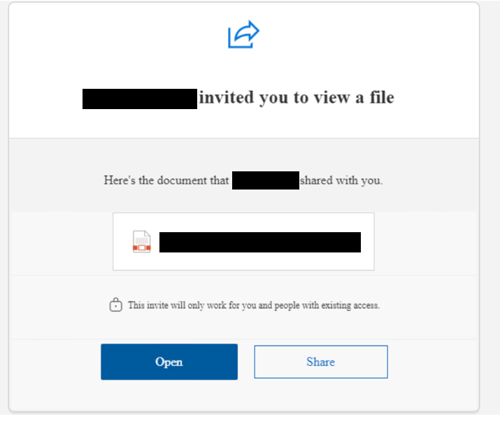
It is likely that the supplier compromise and this attack was by the same threat actor as the email subjects were the same and both emails had malicious documents attached which were hosted in the users personal SharePoint sites.
As seen in the screenshot above, the invitation to open the document would only work for users who had access. Due to this setting, prior to sending the phishing email, the threat actor added internal users to the malicious document and external recipients were added to the link. Within the Microsoft 365 logs, these events are recorded as SharingSet and AddedToSecureLink. Users were granted Read permissions.
Impact
T1565 – Data Manipulation
Numerous file/page and exchange mailbox activities were conducted by the threat actor. All observed were:
- MailItemsAccessed
- HardDelete
- New-InboxRule
- FileAccessed
- Update
- PageViewed
- FileUploaded
- SharingSet
- Create
- Send
- MoveToDeleteItems
- SoftDelete
- Set-InboxRule
- AddedToSecureLink
- SecureLinkCreated
- FolderModified
- FolderCreated
Recommendations
- Implement Multi Factor authentication for all externally accessible accounts
- If not required, disable keep me signed in
- Implement conditional access policies such as enforce MFA for risky sign-ins or block logons from countries not allowed/trusted
- Regularly review Entra ID Security reports such as risky users, risky sign-ins and risk detections
- Conduct phishing exercises to analyse effectiveness of security training
IOC List
|
Value |
Type |
Comment |
|
156.96.154[.]190 |
IP Address |
Threat actor IP address |
|
212.18.104[.]7 |
IP Address |
Threat actor IP address |
|
212.18.104[.]79 |
IP Address |
Threat actor IP address |
|
2a02:4780:10[:]b082::1 |
IP Address |
Threat actor IP address |
|
212.18.104[.]90 |
IP Address |
Threat actor IP address |
|
2a02:4780:10[:]5be5::1 |
IP Address |
Threat actor IP address |
|
212.18.104[.]158 |
IP Address |
Threat actor IP address |
|
212.18.104[.]159 |
IP Address |
Threat actor IP address |
|
212.18.104[.]60 |
IP Address |
Threat actor IP address |
|
surl[.]li |
Domain |
Phishing link |
|
b9n.eadafrive[.]com |
Domain |
Phishing link |