Vendor: SonicWall
Vendor URL: https://www.sonicwall.com/
Versions affected: 10.2.0.8-37sv, 10.2.1.1-19sv
Systems Affected: SMA 100 Series (SMA 200, 210, 400, 410, 500v)
Author: Richard Warren
Advisory URL: https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2021-0026
CVE Identifier: CVE-2021-20045
Risk: CVSS 9.4 (Critical) Summary
SonicWall SMA 100 Series appliances running firmware versions 10.2.0.8-37sv, 10.2.1.1-19sv and below, are vulnerable to multiple stack-based and heap-based buffer overflows in the fileexplorer component, which can be reached by an unauthenticated attacker, calling the sonicfiles RAC_COPY_TO method. These vulnerabilities arise due to the unchecked use of strcpy with a fixed size buffer.
Impact
An unauthenticated remote attacker that successfully exploits any of these issues may be able to execute arbitrary code with the privileges of the nobody user.
Details
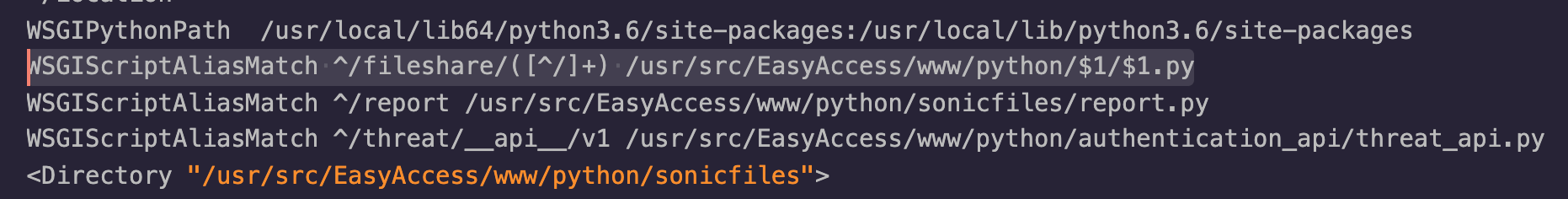
The sonicfiles RAC_COPY_TO (RacNumber 36) method allows users to upload files to an SMB share. The sonicfiles API can be reached by unauthenticated users, via the /fileshare/sonicfiles/ URL.
The following screenshot from the httpd.conf file shows that the /usr/src/EasyAccess/www/python/sonicfiles/fileshare.py WSGI script is aliased via the /fileshare/sonicfiles/ URL:
The RAC_COPY_TO (RacNumber 36) sonicfiles API method maps to the upload_file Python method.
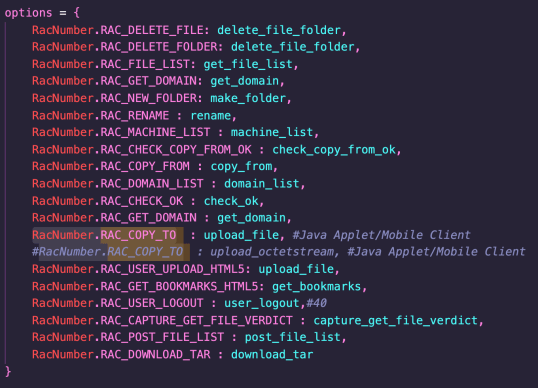
This method simply shells out to the fileexplorer binary with several user-controlled arguments. The filexplorer binary is a custom program written in C++, which is vulnerable to several memory safety issues.
The following screenshot from the upload_file method, shows the user-controllable parameters, Arg1 (fileshare) and Arg2 (filename):
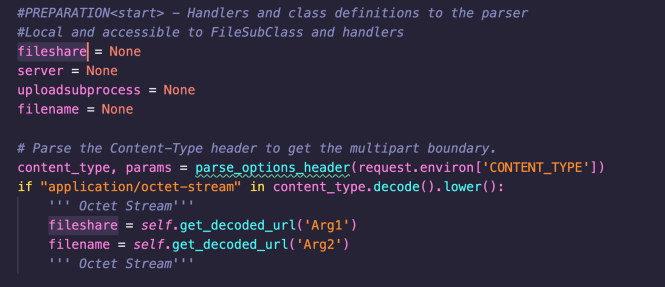
These parameters are appended to a list of arguments which are passed to fileexplorer using Python’s subprocess.popen function.
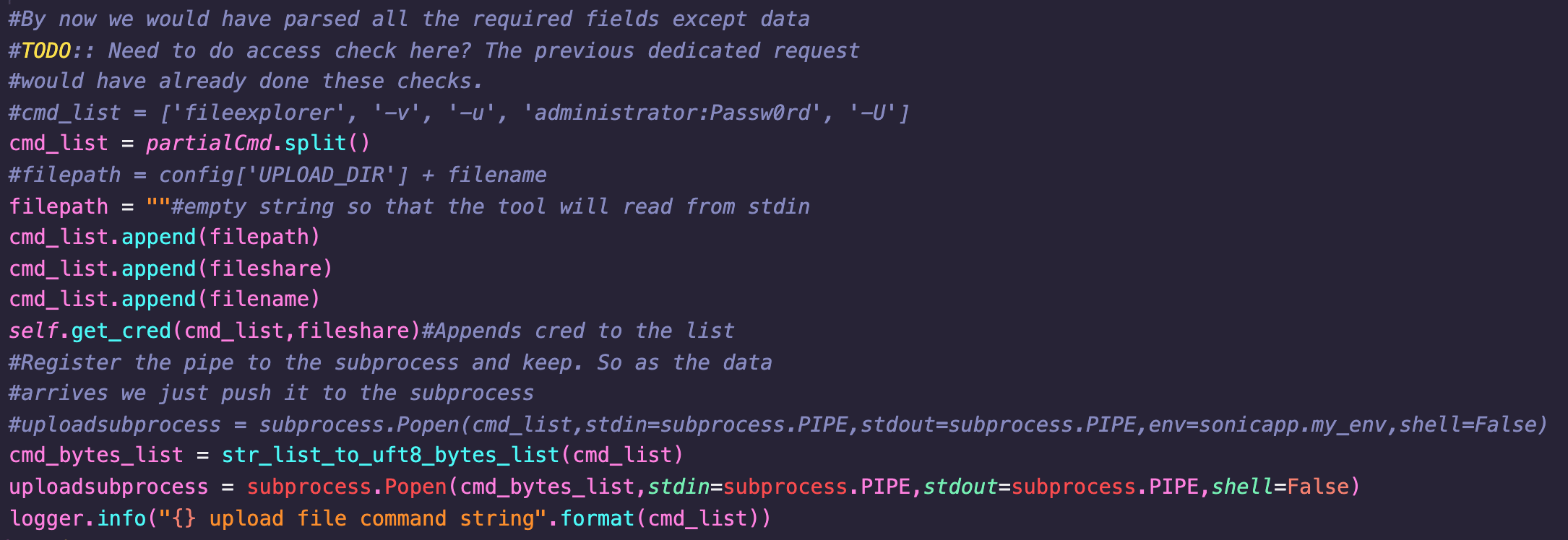
The following decompilation screenshot shows two 128-byte buffers are allocated via a call to MEM_MALLOC, to store the username and password.
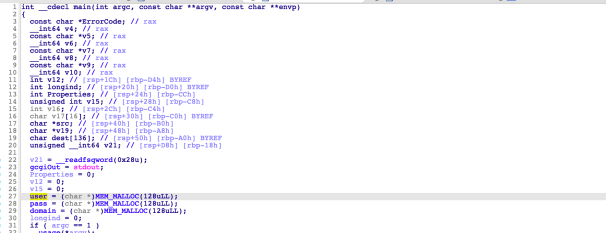
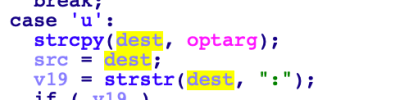
If a -u parameter is supplied, (in the form of user:password), then both the username and password are copied to their respective buffers, with pass being copied using strcpy without checking the length. If only a username is supplied, this is copied to the 128-byte buffer using strcpy. An attacker can control the username and/or password passed in the -u parameter via the User and Pass HTTP parameters.
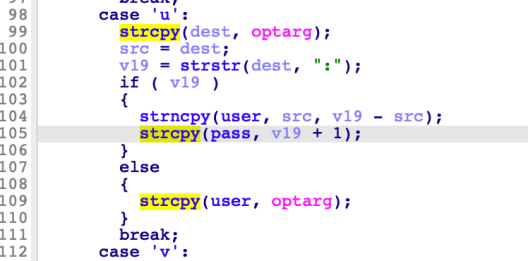
Note there are multiple other heap-based buffer overflows in the argument parsing code resulting from the same pattern, for example, in the -d (domain) parameter, which also allows overflow of a 128-byte heap-buffer. This is likely more exploitable as it is not guarded by a stack-based buffer overflow which limits the size of the payload (see below).
Note on stack-based buffer overflow limitation: In addition to the heap-based buffer overflow issues mentioned above, there is also a stack-based buffer overflow in the username/password parsing code. The code first allocates a 136-byte stack-based buffer. When parsing the -u parameter, the contents are first copied to this buffer without any length checks, resulting in stack-based buffer overflow if the user and/or password is longer than 136-bytes. This means that an attacker can choose between a heap or stack-based overflow by controlling the length of the arguments passed in the User and Pass HTTP parameters, however the attacker is likely to overflow the stack-buffer before they overflow the heap-buffer. Therefore, for heap-based exploitation the -d (HTTP Domn) parameter is likely more exploitable.
Example POST request:
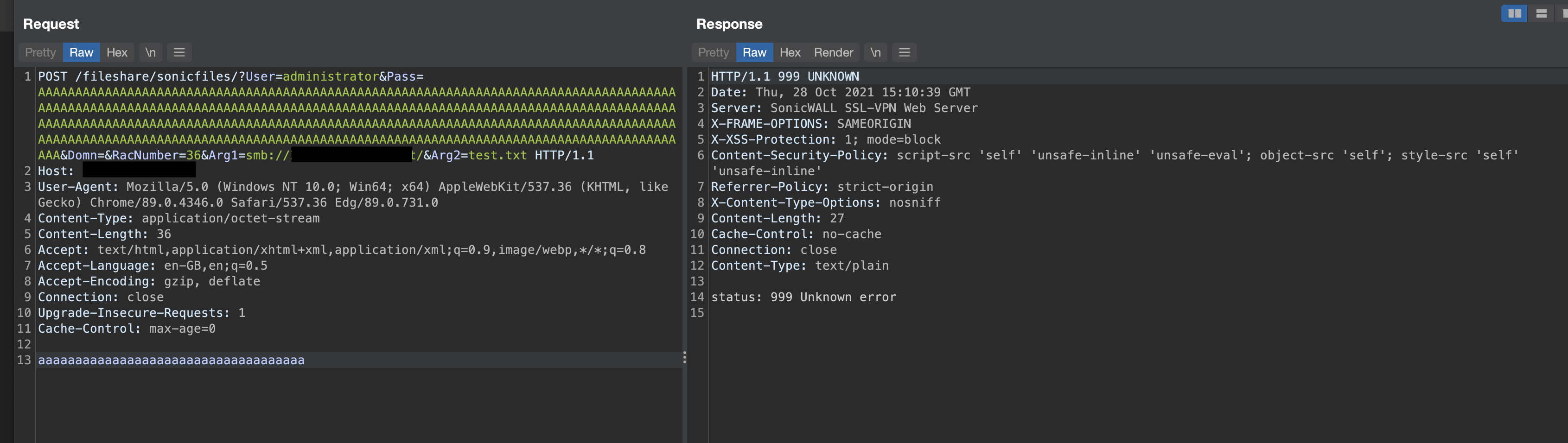
Recommendation
Upgrade to SMA version 10.2.0.9-41sv, 10.2.1.3-27sv or above.
Vendor Communication
2021-10-29 - Vulnerability reported to SonicWall PSIRT.
2021-11-02 - Acknowledgement from SonicWall PSIRT.
2021-12-01 - SonicWall request that NCC Group withhold technical details until 2022-01-11, releasing high-level advisories on 2021-12-09.
2021-12-03 - NCC Group agrees to suggested disclosure timeline.
2021-12-07 - Patch released and SonicWall publish KB article and security advisory.
2021-12-09 - NCC Group advisory released.Thanks to
Jennifer Fernick and Aaron Haymore from NCC Group for their assistance with disclosure.
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published Date: 2021-12-09
Written By: Richard Warren
