In a report [1] by US TV show “60 Minutes” about DARPA [2] and the Internet of Things, the Department of Defence has shown that it can hack the General Motors OnStar [3] system to remotely control a last-generation Chevrolet Impala.
DARPA has been investigating the cyber security of vehicle systems and many other embedded devices in what is known at the HACMS (High Assurance Cyber Military Systems) programme [4].

Although the technical details of the attack have not been publicly revealed by DARPA, the techniques used to perform this attack most likely originated in some academic research performed in 2010 and quoted [5] by DARPA in a presentation [6] entitled “DARPA Cyber Analytical Framework”. The quote was:
“[a] small group of academics took control of a car using Bluetooth and OnStar. They were able to disable the brakes, control the accelerator, and turn on the interior microphone”
This original research was also presented [7] at the Usenix Security Symposium in August 2011.
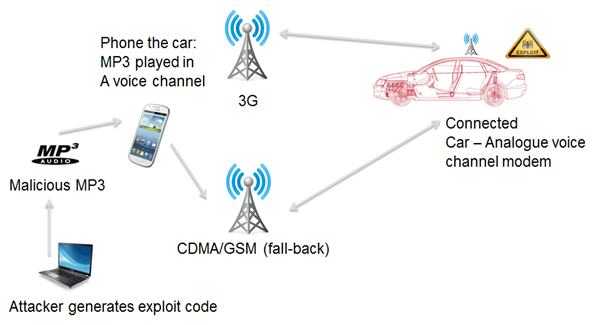
Remote attack against TCU fallback analogue modem
Assuming that this is the attack that DARPA has replicated some of the technical details of how the attack works are described below:
- Due to cellular coverage issues, the TCU (Telematics Control Unit) embedded in the vehicle has a fall-back mechanism it can use when a 3G mobile signal is not available: A CDMA/GSM analogue modem.
- The researchers reverse-engineered the software modem protocol parser, which is the code that interprets modem data that arrives at the device.
- A buffer overflow [8] vulnerability was identified as the result of incorrect assumptions by:
- The TCU manufacturer
- The TSP
- The TCU manufacturer assumed a fixed length data packet would be received by the device, but the TSP (Telematics Service Provider) assumed the data packet could be any length.
- A trivial buffer overflow vulnerability in a memcpy() function call could then be exploited to fully control car functions, as the TCU was connected directly to the CAN bus [9], which is the network on which the cars ECUs [10] communicate and control critical functions such as the steering, braking etc.
- As the vulnerability is in the software modem that processes data sent by modulating a carrier signal in the audio voice channel, the attack can be performed by phoning the TCU and playing it a specially crafted MP3 audio file.
- A summary of the attack is shown below:
How could the attack have been prevented?
- The memcpy() buffer overflow vulnerability (the root cause of the problem) would likely have been identified in a source code review of the software modem within the TCU
- The TCU manufacturer should not have made assumptions about the validity of the data being supplied to it via its interfaces
- The TCU should not accept voice or data calls from any unauthorised number e.g. not originating from the TSP
At NCC Group we regularly perform product security reviews for automotive components e.g. a recent engagement for Zubie. [11] Also, our partnership [12] with automotive experts SBD resulted in the development of the ASDL (Automotive Secure Development Lifecycle) [13] which is the long term cyber security assurance solution for automotive OEMs and their suppliers.
- [1] http://www.cbsnews.com/news/car-hacked-on-60-minutes/
- [2] http://www.darpa.mil/default.aspx
- [3] https://www.onstar.com/us/en/home.html
- [4] http://www.darpa.mil/Our_Work/I2O/Programs/High Assurance_Cyber_Military_Systems_(HACMS).aspx
- [5] http://www.autosec.org/pubs/cars-oakland2010.pdf
- [6] www.darpa.mil/WorkArea/DownloadAsset.aspx?id=2147484449
- [7] https://www.youtube.com/watch?v=bHfOziIwXic
- [8] http://en.wikipedia.org/wiki/Buffer_overflow
- [9] http://en.wikipedia.org/wiki/CAN_bus
- [10] http://en.wikipedia.org/wiki/Engine_control_unit
- [11] http://zubie.co/2014/11/07/110614/
- [12] 2014/10 SBD post
- [13] 2014/10 asdl post
Published date: 12 February 2015
Written by: Andy Davis
