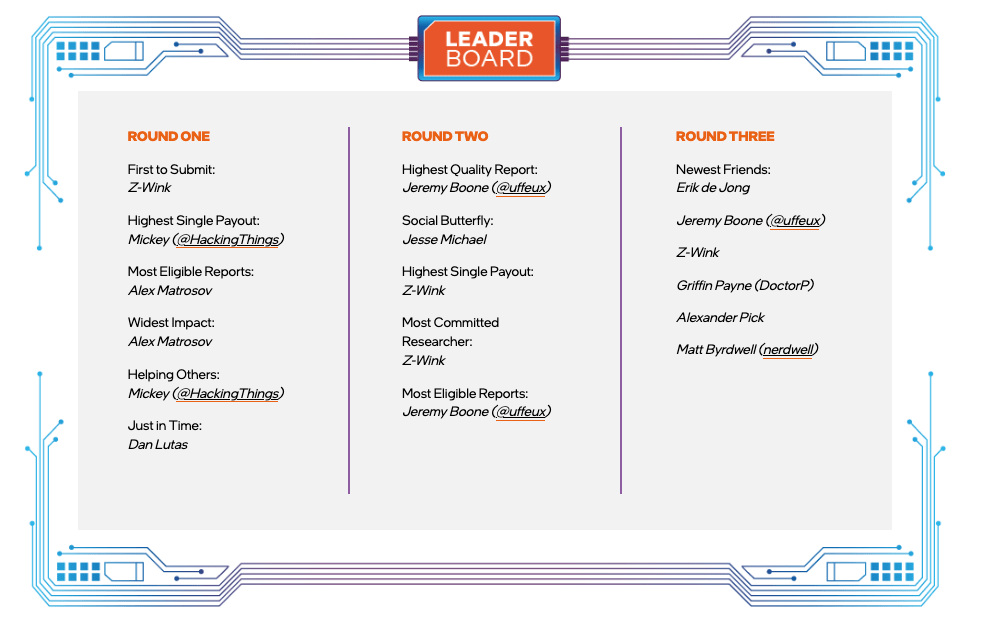
Congratulations to NCC Group researcher Jeremy Boone, who was recently recognized for both the Highest Quality Report, as well as the Most Eligible Reports, as an invited researcher to the Intel Circuit Breaker program!
From Intel:
“This exclusive event invited a select group of security researchers to hunt vulnerabilities in the 11th Gen Intel® Core™ vPro® platform.… Potential findings might involve any of the following:
- Micro-architectural attacks
- Firmware attacks like microcode
- Platform configuration (Intel® vPro, Intel® Management Engine, etc.)
- Platform design
- Physical attacks (note that this is a deviation from our existing Bug Bounty policy)
- Firmware attacks
- Physical: I/O, storage, flash, memory, sensors, embedded controller, trusted platform module
- Firmware: BIOS, IP firmware components, embedded controller, sensor, trusted platform module, storage, flash storage
- Device drivers shipped with the device (such as Intel graphics drivers, Thunderbolt device drivers, Bluetooth device drivers, wireless drivers, ethernet drivers, chipset driver)
Jeremy Boone is a Technical Director in our Hardware Embedded Systems practice, serving as mentor and leader to researchers across our hardware research program. He is perhaps best known for his research, TPM Genie, an I2C bus interposer for discrete Trusted Platform Modules
Congratulations Jeremy!
