Created by Dan Hastings and Emanuel Flores
Solitude is an open source privacy analysis tool that enables you to conduct your own privacy investigations into where your private data goes once it leaves your web browser or mobile device. Whether a curious novice or a more advanced researcher, Solitude makes the process of evaluating an app’s privacy accessible for everyone.
Motivation
Oftentimes the only way for the end user to figure out where their private data goes once they enter it into a web application or mobile device is through the apps’ privacy policy. Privacy policies not only have a notorious history of being difficult to understand but don’t always tell the truth about an application’s data collection practices. As shown through previous research from NCC Group at the Defcon 27 Crypto and Privacy Village[1], more often than not there can be discrepancies between an app’s privacy policy and the actual data collection practices of the app[2]. Solitude was built to make proxying your web and mobile traffic easier and make the process of conducting privacy investigations of your favorite apps more streamlined and straight forward. The process of searching for large amounts of data in an HTTP intercepting proxy such as Burp suite can be quite cumbersome and tedious. Solitude automates the process of searching for specific configured data by recursively decoding requests automatically. Solitude can be configured to look for any data that you input in a mobile or web application and reveal where that data is going.
Features
- Recursively decodes base64 and url encoded data
- Supports protobuf at the first layer of decoding
- Searches for sha1, sha256 and md5 hashes of all configured data
- Searches for internal IP addresses
- Searches for GPS coordinates
- Configured data is converted into YARA rule sets
Usage and Design Decisions
Solitude was designed to prioritize the investigation of mobile applications. Proxying mobile traffic from a mobile device can be difficult as mobile applications are not web browsers and are not always able to easily route traffic to an HTTP proxy. With this in mind, Solitude uses a VPN server on your computer to route all traffic from the VPN server to Solitude.
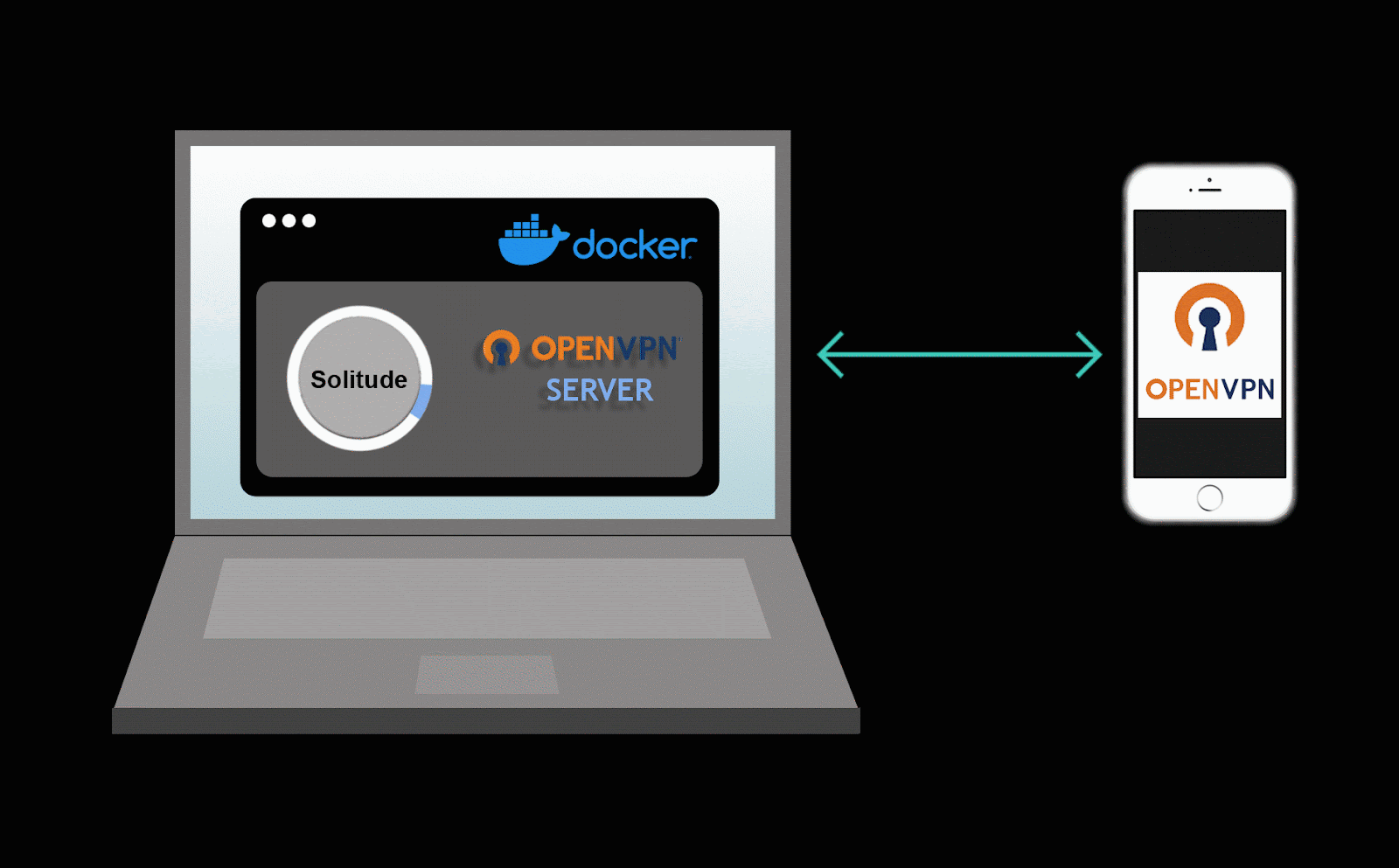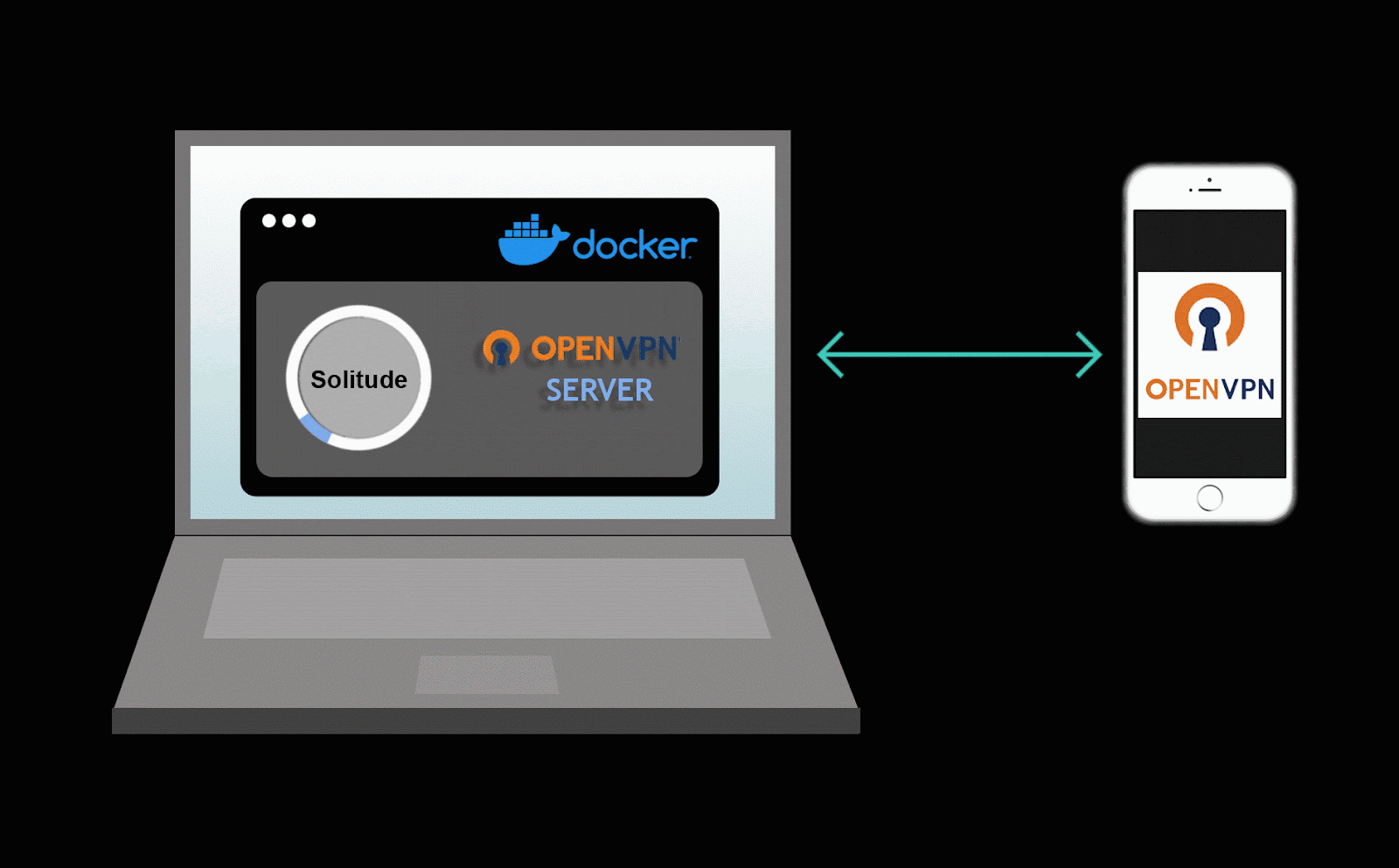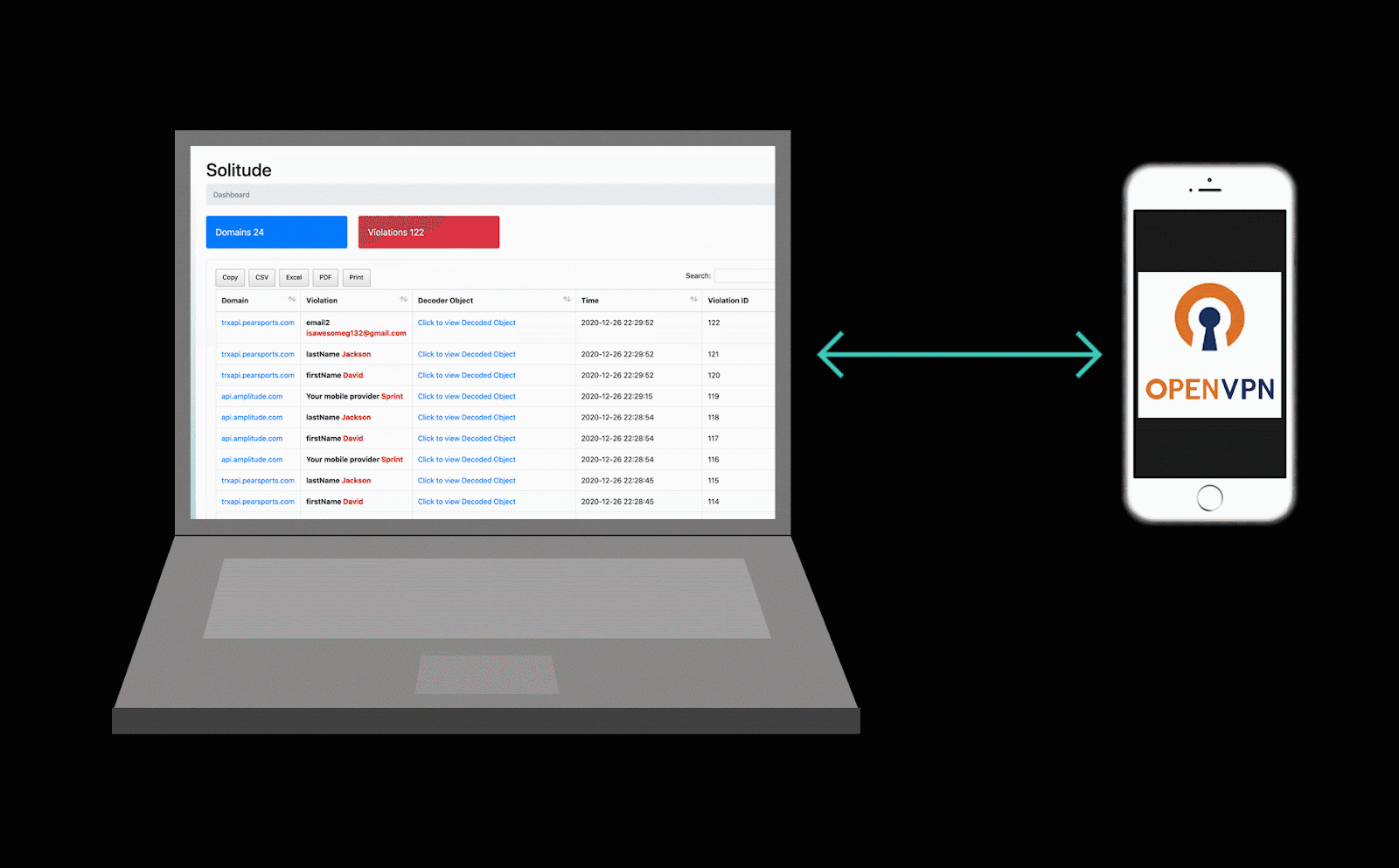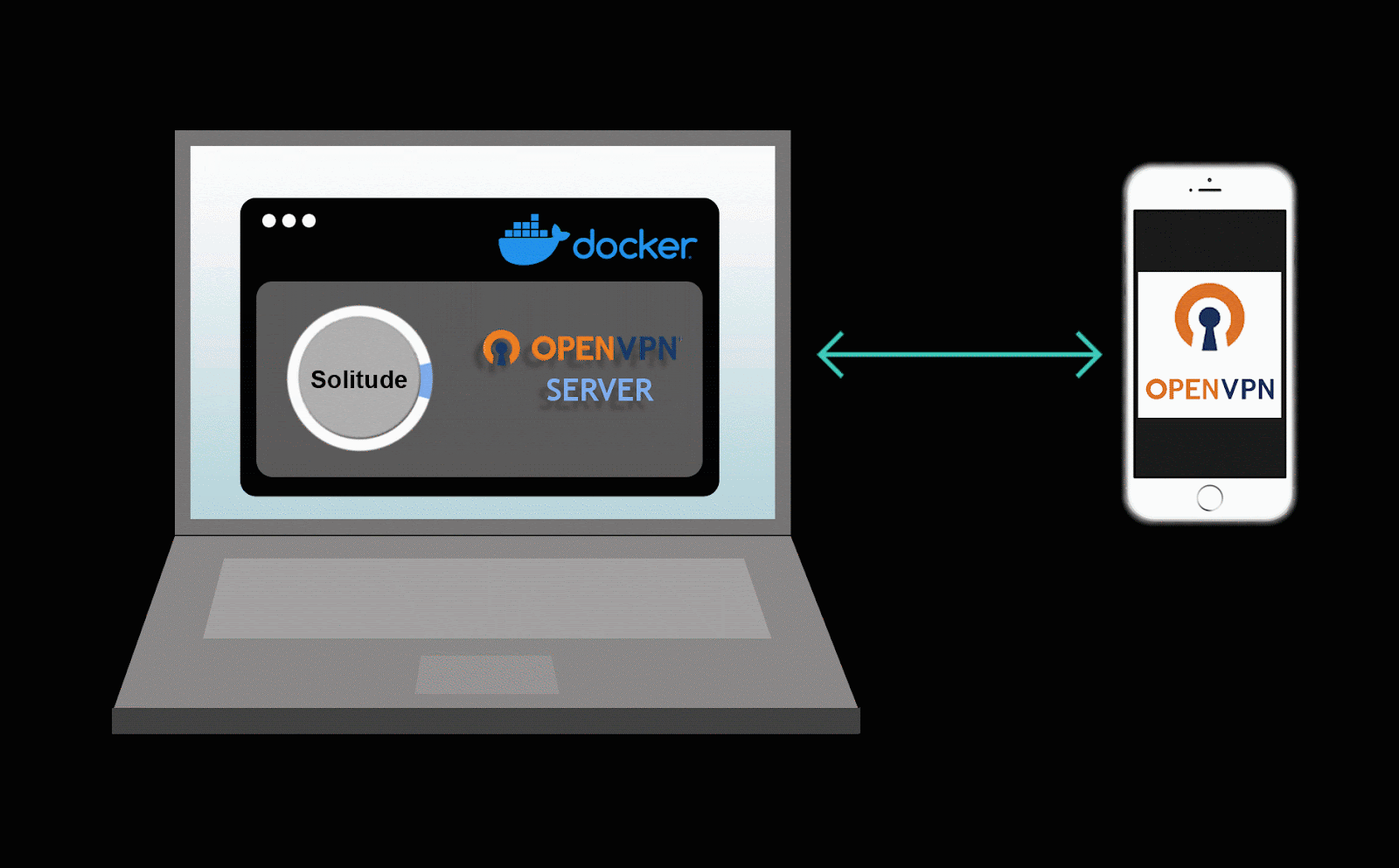
For sending mobile traffic to Solitude. Solitude makes use of a VPN server running inside a docker container. Graphic courtesy of Chelsea Raflo.
The second method of running Solitude is intended for users who want to inspect web applications in a browser. Just like you would forward traffic to an intercepting HTTP proxy such as Burp Suite in your browser you configure your browser to forward traffic to Solitude.
Configuration
In order to configure Solitude to search for personal information, a user must place the data they want searched for the myrules.json configuration file. The configuration must be a key value pair in the format of a JSON object. An example would be {“phoneNumber”: “555-555-5555”}. Once data is configured on startup the phone number is converted into a Yara rule and searched for in every single HTTP request and websocket message emitted from the browser or mobile device that is configured with Solitude.
Architecture
Solitude consists of several main components to help and facilitate tracking personally identifiable information (PII) to third parties. In it’s main form of operation, Solitude runs as two stand alone Docker containers. One is dedicated to running the solitude web app, openVPN, and proxy. While the second container runs a mysql database container to store previous connections and violations.
A user will connect their device to the openVPN server which allows all traffic to be routed through Solitude. Inside the docker container, the traffic is routed through MitMProxy using a script that analyses all HTTP and websocket traffic by searching through Yara rules. All connections are logged for future auditings and any connection found to be in violation of one of the configured rules is logged for display in the web app.
To facilitate the management and start up of the containers, the docker-compose tool is used which supplies the required options to ensure the containers start up properly.
Conclusion
Solitude is a privacy enhancement tool meant to empower people to inspect their favorite apps to see where the data the apps collect about them goes.
You can find a demo of Solitude and a more in depth talk from this year’s CCC (rC3) at:
https://media.ccc.de/v/rc3-987025-solitude or
https://www.youtube.com/watch?v=zz6ST0VWtQI
Solitude is open source and is available for download on the NCC Group GitHub repository:
https://github.com/nccgroup/solitude
References
[1] Ironically, iOS robocall-blocking apps are violating your privacy: Defcon 27 Privacy and Crypto Village https://cryptovillage.org/dc27/
