Summary
On the 6th of April 2022, NCC Group’s Fox-IT discovered two separate flaws in FUJITSU CentricStor Control Center V8.1 which allows an attacker to gain remote code execution on the appliance without prior authentication or authorization.
The vulnerability is caused due to a lack of user input validation in two PHP scripts, which are normally included post-authentication. As no include-guards are in-place, an attacker is able to trigger the script without prior authentication by calling it directly.
These are tracked as CVE-2022-31794 and CVE-2022-31795
Impact
An attacker is able to take control over the appliance as if they were logged in directly via a secure shell. If exploited, the attacker obtains limited user privileges on the machine as the “www-data” user; however, it should be noted that the Kernel on the system which NCC Group’s Fox-IT encountered is severely outdated, allowing an attacker to easily escalate their privileges to the administrative “root” user of the system.
Due to the sensitive nature of the system, any attacker with full control over the system is potentially able to read, modify and potentially destroy the entire virtual backup tapes, which could be used as an initial stage of a ransomware attack to ensure the victim is not able to recover and is forced to pay the ransom.
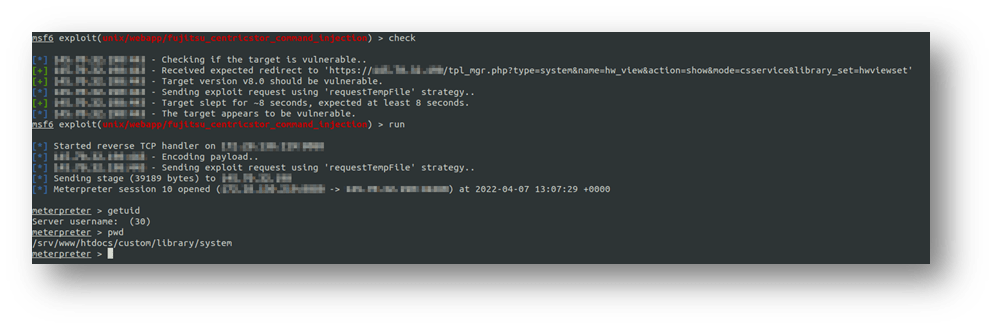
The following screenshot shows how NCC Group’s Fox-IT was able to gain remote code execution on the appliance using a custom-built Metasploit[1] module:
Details
During a recent penetration test at one of NCC Group’s Fox-IT’s clients, a full review was performed of the backup process, as well as any appliances used, as to ensure the company has full system backups in the event of a ransomware breakout. One of the appliances in question was the FUJITSU CentricStor Control Center. Fox-IT requested read-only access to the appliance in order to assess the security of the product.
The web-application used to manage the backups was inspected, which lead NCC Group’s Fox-IT to discover the existence of two scripts, which are accessible by any user on the network and which pass user input directly to the “shell_exec” and “system” functions.
The two files in questions are as follows:
/srv/www/htdocs/custom/library/system/grel.php/srv/www/htdocs/custom/library/system/hw_view.php
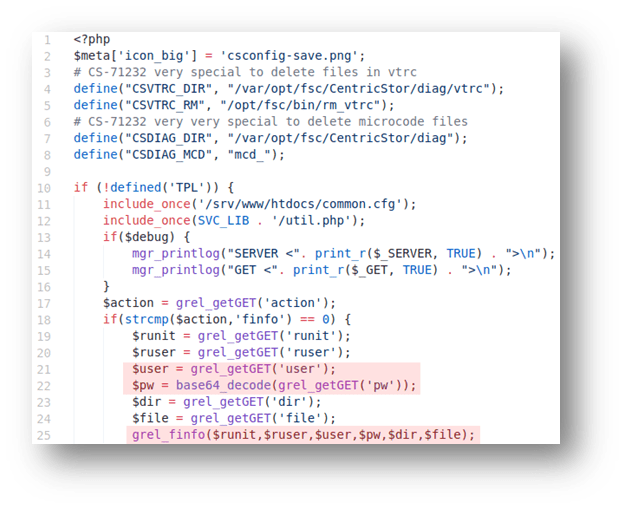
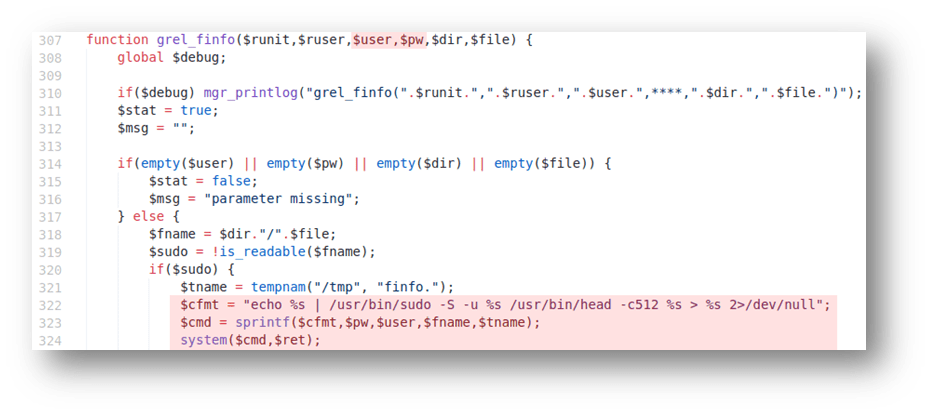
Command injection in grel.php (grelFileInfo)
The first vulnerability resides in the “grel_finfo” function in grel.php. An attacker is able to influence the username (“user”), password (“pw”), and file-name (“file”) parameters and inject special characters such as semicolons, backticks, or command-substitution sequences in order to force the application to execute arbitrary commands. The following screenshots show this in more detail:
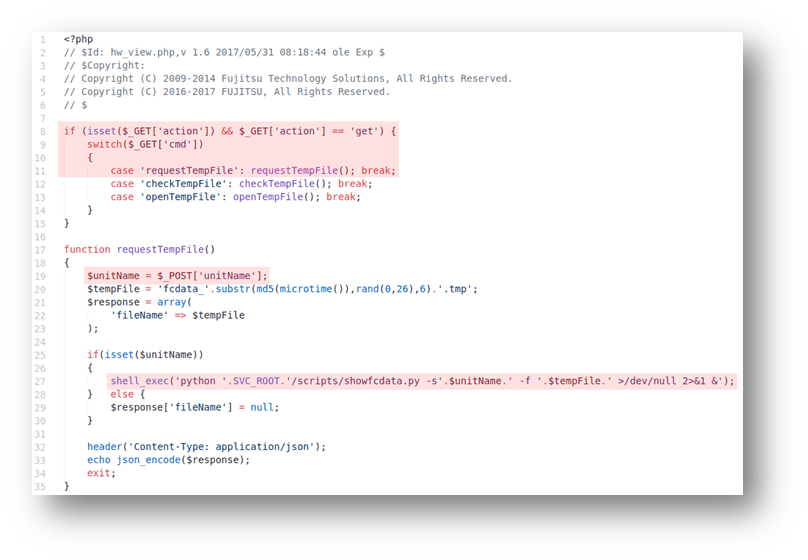
Command injection in hw_view.php
The second vulnerability resides in the "requestTempFile" function in hw_view.php. An attacker is able to influence the “unitName” POST parameter and inject special characters such as semicolons, backticks, or command-substitution sequences in order to force the application to execute arbitrary commands. The following screenshot shows this in more detail:
Recommendation
Upgrade the product to versions v8.1A SP02 P04 or v8.0A SP01. Unfortunately, a dedicated Fujitsu customer request is required to do this due the software distribution model. For more information please contact Fujitsu through their ServiceNow Portal or Support Assistant.
Lastly, block any inbound traffic to port 80 and 443 through the use of a network firewall. Traffic should be selectively allowed only to other instances of the appliance, and only made directly accessible through a management LAN. This ensures attackers are not able to reach the machine without gaining access to this network segment first.
Another temporary measure to secure the application for the time being could be to force the web-interface to bind to the local loopback interface (127.0.0.1) and using a reverse SSH forward to access the service that way. This ensures no attackers are able to reach the web-interface before authenticating over SSH first. Please note that this might void your warranty, as such it is not recommended.
Vendor Notice
Footnotes
1. https://en.wikipedia.org/wiki/Metasploit_Project
2. https://www.offensive-security.com/metasploit-unleashed/about-meterpreter/
3. https://www.php.net/manual/en/function.escapeshellarg.php