Carnivore is a tool for assessing on-premises Microsoft servers such as ADFS, Skype, Exchange, and RDWeb. Carnivore’s functionality covers every stage an attacker would follow – from discovering relevant subdomains, to uncovering username format and username enumeration, to password spraying and additional post authentication activities for Skype such as retrieving the global address list or lists of meetings for compromised users. The post authentication tasks are performed using the UCWA API and do not constitute new exploits against these servers.
It is hoped that by making potential flaws more easily detectable during penetration tests, gaps in organisations’ defences that have potentially been forgotten about can be spotted and closed. An example of this is that Carnivore searches for numerous uncommon NTLM authentication points, and will find endpoints for username enumeration and password spraying separately. This means that while well known and often tested login portals might have been hidden from public view, Carnivore will help uncover entry points into the domain that might have gone unnoticed.
This blog post will focus on a single use case, from start to finish. Future posts will cover a deeper dive into some of the research and statistics that have informed choices made along the way as well as covering “weaponisation” of the UCWA API. For further detail, please see the following:
Carnivore is designed to unlock tabs as testing progresses and new options become available. You will see the Address Book or MeetingSnooperTM tabs unlock once valid credentials have been recovered, for example. To start with, we are going to attempt to find all Microsoft servers for the “nevtek.nev” domain. As you can see, we have also selected “Attempt to Discover Internal Domain Information (Active) as this will send a blank Type 1 NTLM message to relevant endpoints and pull back the internal domain name required to make password guesses.
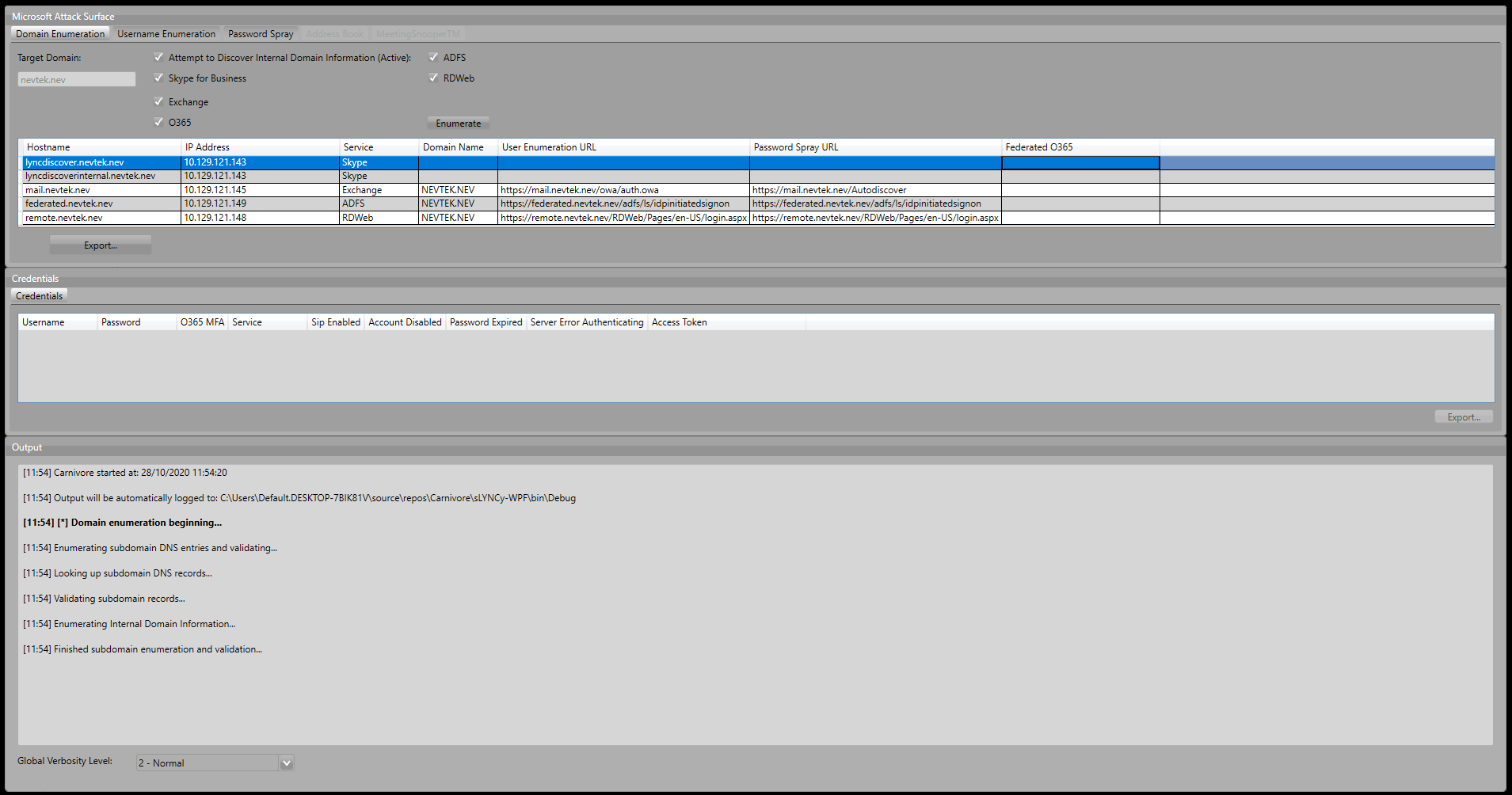
Carnivore has uncovered a server for each service – these are validated both in terms of removing false positives from wildcard DNS resolutions, and also that the server responded as expected for that specific service. URLs required for the timing-based username enumeration and password spraying have been separately detected and verified.
Moving on to the Username Enumeration tab we leave the defaults set and click Enumerate Users. Carnivore now uses Smart Enumeration to determine the username format by trying 9 different types of username format until a pattern emerges amongst the usernames found to be valid. In this case, the format is found to be jsmith.
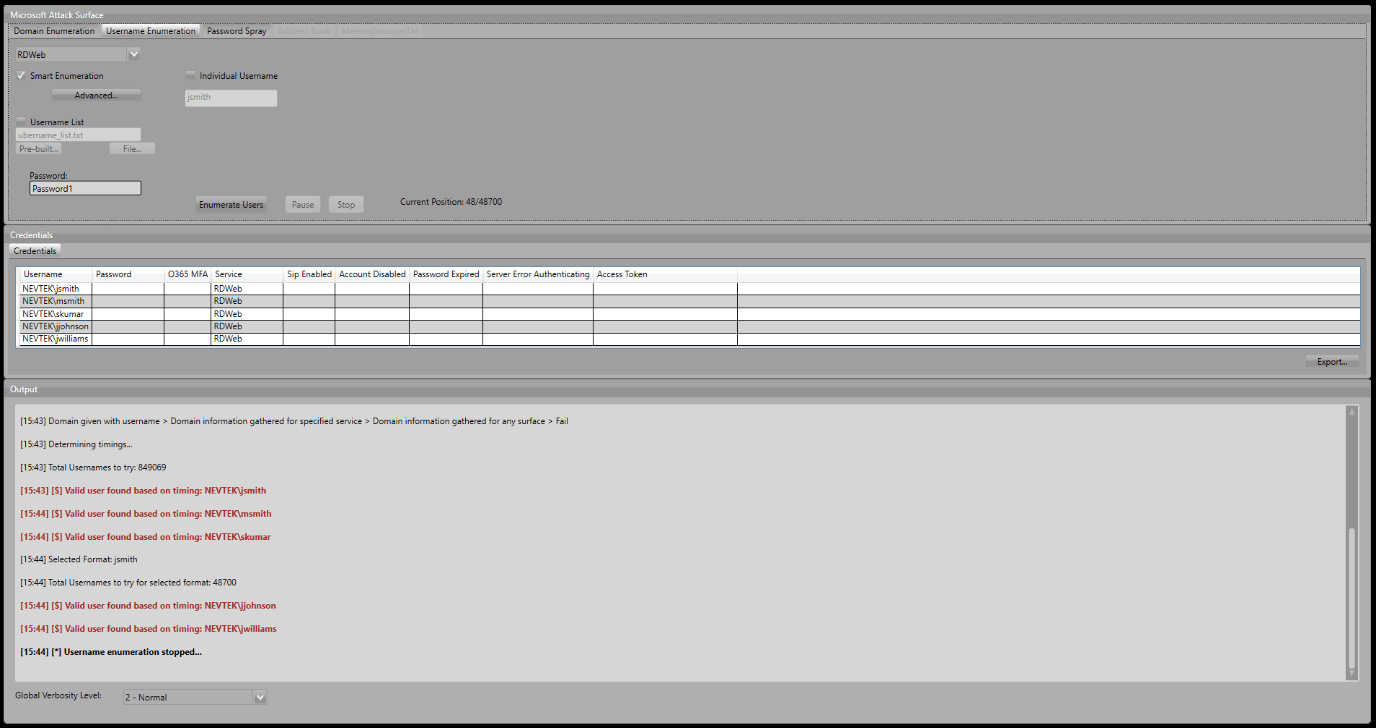
Username enumeration can take around 30 seconds for each invalid user, meaning that to leave this to finish could take days, so instead, we now pause the enumeration and move to the Password Spraying tab. We know the likely format in use, and can now spray all the built-in usernames of that format in around 10 minutes. We select the format from the drop down list, change the password to something likely – in this case Summer2020 – and hit Spray.
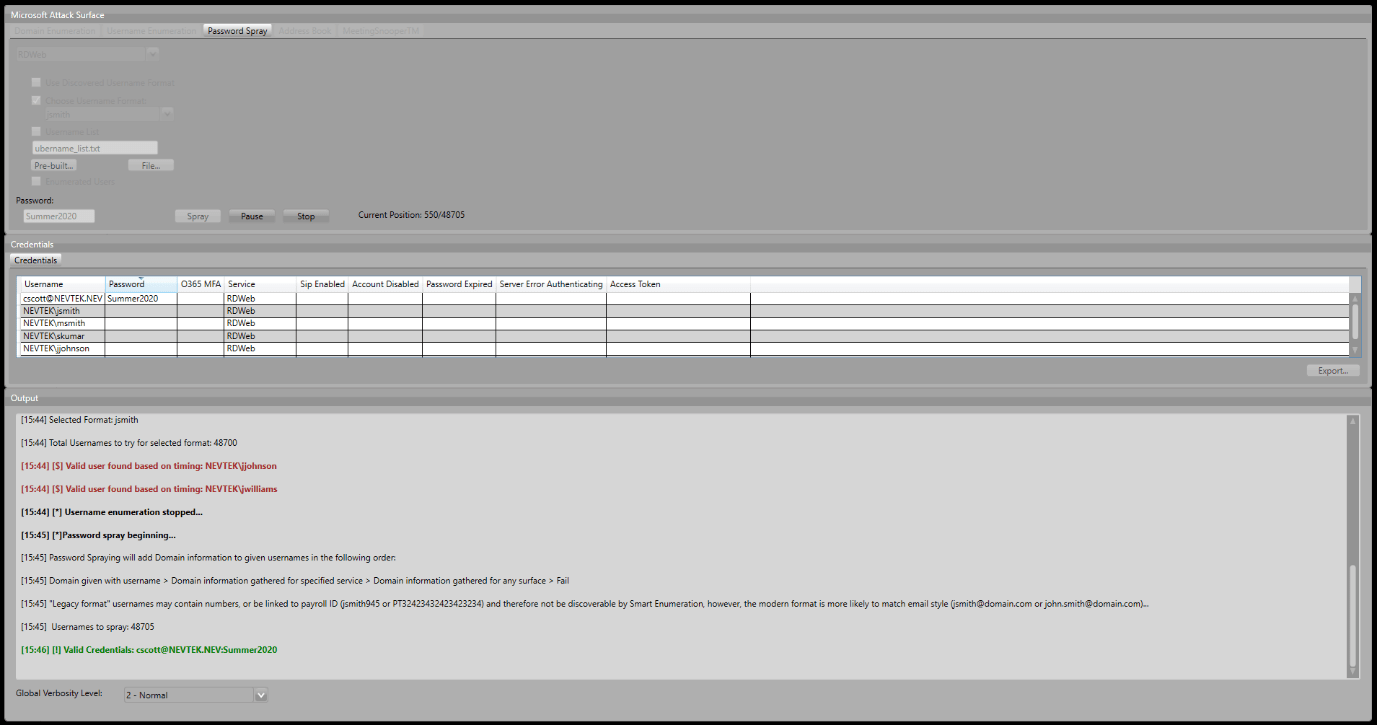
Once valid credentials have been recovered, the Address Book and MeetingSnooperTM tabs become unlocked. Once the spray is done, we move to the Address Book tab. Again, we can leave the defaults set and click Go. This recursively searches with the UCWA API to pull back users from the address book, including a raft of information such as their email address, job title, office location, and phone number.
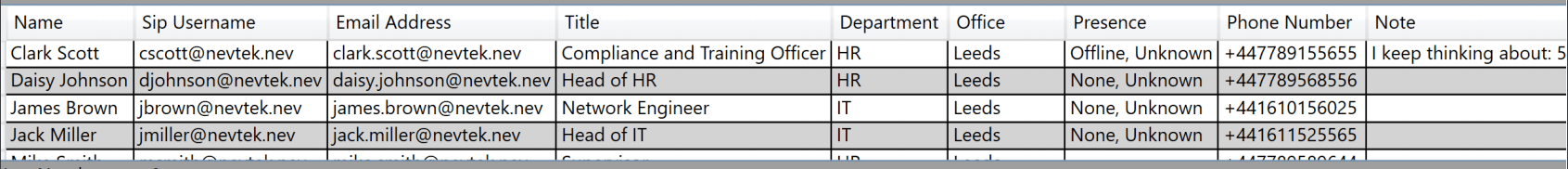
This information would be invaluable to inform the next stages of an attack. The names can be converted manually to the discovered format and fed back in to password spraying activities, or the details such as phone number and office location could be used for social engineering. It is important for organisations to know that these sorts of attacks are possible, and that using a route such as the one described above may enable attackers to authenticate to Skype for Business, which is often seen as a trusted internal communications tool. This also highlights the importance of strong internal password policies, as services such as these may expose user accounts to attacks from the outside, and a compromised account can then be used as a foothold into the organisation.
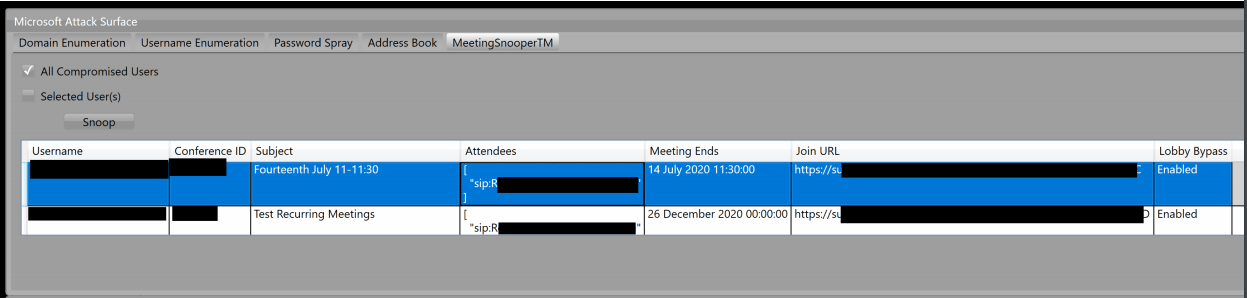
The final post authentication function of Carnivore is MeetingSnooperTM. While the name chosen is tongue in cheek, it highlights a critical attack vector for the Skype for Business server that defenders need to be aware of. A weak internal password leading to a set of compromised credentials as described above could then be used with the legitimate UCWA API to return a list of scheduled meetings for that user. This includes the information needed to join the meeting as the compromised user. More often than not it is likely that a number of accounts will be compromised, providing a list of potential users and meetings to join. An attacker would be able to repeatedly check for new meetings for users that interested them – C-suite executives, security team members, the head of financial fraud investigations, and so on. While joining a meeting would not be fool proof – it would be possible the presence of an additional party would be called out and the meeting cancelled – as the attacker would show up as the compromised user who may also be in attendance this may well be chalked up to a glitch, and if no-one was signed into the application, it is possible no-one would even know an additional party was in the meeting.
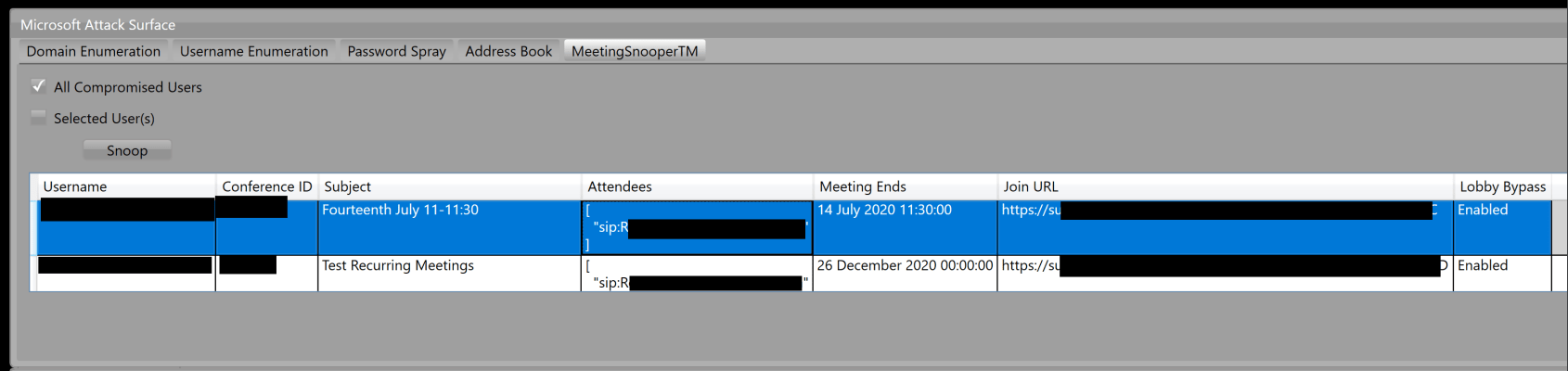
Hopefully this walkthrough of a simple use case has shown a number of potential areas of concern relating to externally accessible, on-premises Microsoft servers and how Carnivore can be used to help easily uncover and highlight these areas during penetration tests.
For further information:
